Understanding Unsecure Domain Configurations in Microsoft 365
As we kick off 2025, it’s timek to revisit an often overlooked but critical aspect of Microsoft 365 security: unsecure domain configurations. In this post, we’ll dive into what these configurations are, the risks they pose, and how you can address them to fortify your environment. Let’s get started!
What Are Unsecure Domain Configurations?
Microsoft Defender for Identity continuously monitors your environment for domain configurations that may expose your organization to security risks. When such configurations are identified, they are flagged as unsecure domain configurations.
In simple terms, these are misconfigurations in your domain’s settings that leave it vulnerable to attacks. Think of it as leaving your house doors unlocked—it might seem harmless at first, but it’s an open invitation for trouble.
What Risks Do Unsecure Domain Configurations Pose?
Failing to secure your domain configurations can create opportunities for malicious actors. These vulnerabilities often serve as entry points for attackers, enabling them to infiltrate your systems quietly and efficiently.
For example, if LDAP (Lightweight Directory Access Protocol) signing isn’t enforced, attackers can exploit this gap to compromise domain accounts. This becomes especially dangerous if those accounts have privileged access to other resources.
One such attack scenario is KrbRelayUp, where an attacker uses insecure LDAP communication to gain unauthorized access. Such breaches can result in:
- Compromised sensitive data
- Escalated privileges
- Disruption of business operations
Why Should You Secure Your Domains?
Securing your domain configurations is essential to:
- Prevent unauthorized access: Mitigate risks associated with common attack vectors like man-in-the-middle attacks.
- Protect sensitive data: Ensure that privileged accounts are shielded from exploitation.
- Maintain compliance: Meet regulatory and organizational security requirements.
- Strengthen your overall security posture: Reduce your attack surface and improve your Secure Score in Microsoft 365.
How to Identify and Fix Unsecure Domain Configurations
Step 1: Use the Security Assessment Tool
Head over to the Microsoft 365 Secure Score dashboard. Here, you can:
- Identify domains with unsecure configurations.
- Review top impacted entities.
- Access actionable recommendations for remediation.
Step 2: Review Recommendations
For each identified issue, Microsoft provides tailored remediation steps. Below are examples of common issues and how to address them:
| Recommended Action | Remediation | Reason |
| Enforce LDAP Signing policy to “Require signing” | Require domain controller-level LDAP signing. Learn more here. | Unsigned network traffic is vulnerable to man-in-the-middle attacks. |
| Set ms-DS-MachineAccountQuota to “0” | Set the ms-DS-Machine-Account-Quota attribute to 0. Learn more here. | Limits non-privileged users from registering devices in the domain. |
Step 3: Take Action
- Modify or remove insecure configurations based on the provided recommendations.
- Validate changes to ensure compliance with Microsoft’s best practices.
Step 4: Monitor Progress
While recommendations are updated in near real-time, note that:
- Scores and statuses are updated every 24 hours.
- Impacted entities lists update within minutes of applying fixes, but their statuses might take time to reflect as “Completed.”
How to Configure LDAP Signing
Step 1: Open Group Policy Management
On a domain controller or a system with Group Policy Management tools installed, open the Group Policy Management Console (GPMC).
Create a new Group Policy Object (GPO) or edit an existing one linked to the domain controllers.
Step 2: Navigate to the Relevant Setting
In the GPO editor, go to Computer Configuration > Policies > Windows Settings > Security Settings > Local Policies > Security Options.
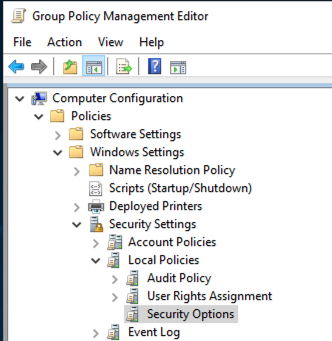
Locate the policy named Domain controller: LDAP server signing requirements.
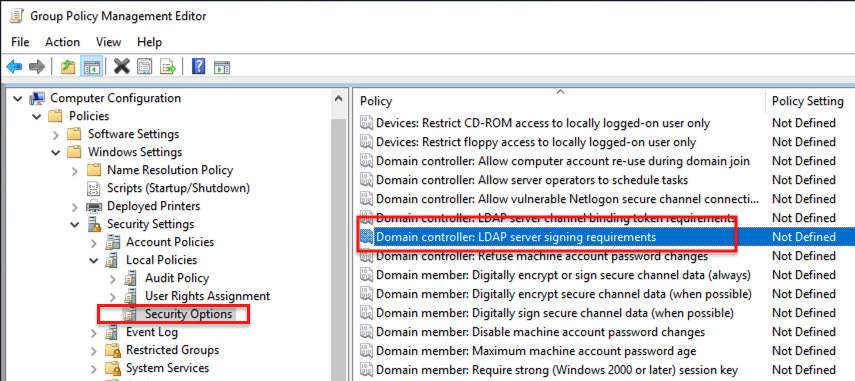
Step 3: Configure the Policy
Double-click the policy and set it to Require signing.
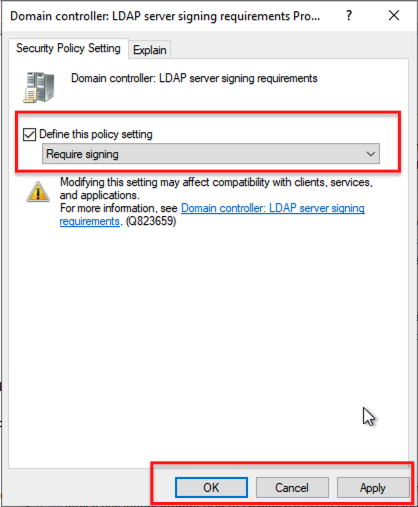
You will be presented with a confirmation of change notification when you click Apply.
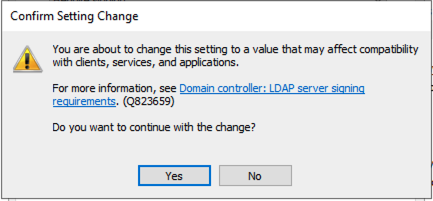
Important Note on Warnings
When configuring LDAP signing, you may encounter a warning message like the one shown above. This is a reminder that enforcing LDAP signing could impact legacy applications or clients that do not support it. Ensure compatibility by testing in a controlled environment before applying the policy broadly.
Click Yes.
Step 4: Update Group Policy
Run the following command on all domain controllers to ensure the policy is applied:
|
1 |
gpupdate /force |
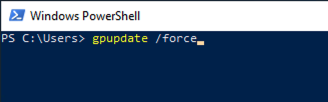
Verify the configuration by checking the event logs or running LDAP-specific tools.
How to Set ms-DS-MachineAccountQuota to “0”
Step 1: Open Active Directory Users and Computers
- Log in to a domain controller or a system with the Active Directory Users and Computers snap-in installed.
- Navigate to the domain root in the console tree.
Step 2: Access Attribute Editor
Right-click the domain name and select Properties.
Go to the Attribute Editor tab.
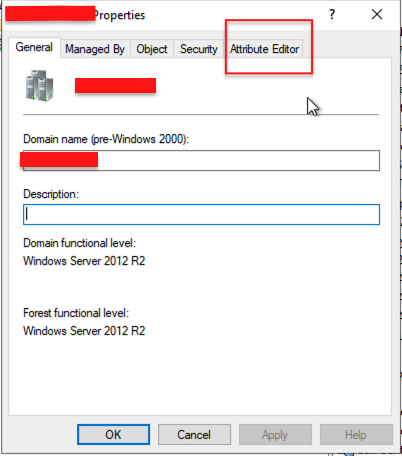
Locate the attribute ms-DS-MachineAccountQuota.
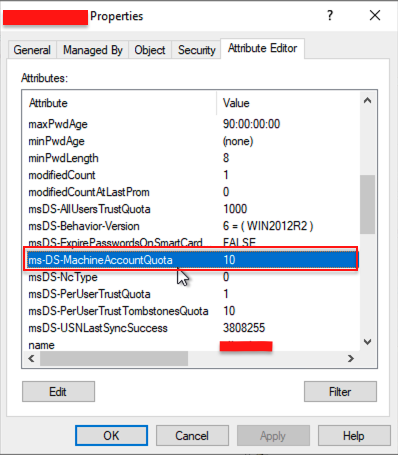
Step 3: Modify the Attribute
- Select the ms-DS-MachineAccountQuota attribute and click Edit.
- Change the value to 0 and click OK.
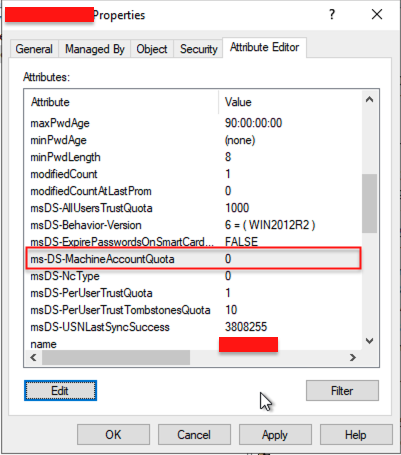
Step 4: Verify Changes
- Run the following PowerShell command to confirm the new value:
- Get-ADDomain | Select-Object Name, ms-DS-MachineAccountQuota
- Ensure the output reflects the updated value of 0.
Final Thoughts
Addressing unsecure domain configurations isn’t just a box to check—it’s a foundational step in safeguarding your Microsoft 365 environment. By proactively identifying and remediating vulnerabilities, you’re not just protecting your organization today but also fortifying it against future threats.
As you start implementing these recommendations, remember: every action you take toward securing your domains helps reduce your attack surface and ensures a safer, more reliable environment for your users.

Be First to Comment