Optimizing Security Operations: Seamless Integration of Microsoft Sentinel with Defender XDR in the Unified Defender Portal
Introduction
Microsoft Sentinel, now part of the public preview for the unified security operations platform in the Microsoft Defender portal, brings together Microsoft Defender XDR for enhanced incident management and advanced hunting. This integration reduces tool switching and creates a more context-focused investigation process, expediting incident response and helping to stop breaches faster. As of April 2024, this integration is in preview and may undergo significant changes before its full release.
Benefits of Microsoft Sentinel and Defender XDR Integration
- Unified Incident Management: Combines Microsoft Sentinel’s comprehensive SIEM capabilities with Defender XDR’s incident response tools in a single platform.
- Enhanced Threat Hunting: Utilizes advanced hunting capabilities across different datasets within a single portal, improving efficiency and reducing the need for context-switching.
- Streamlined Operations: Aligns incident management processes and advanced threat detection tools across both platforms, offering a cohesive security operations strategy.
Prerequisites
Before you can integrate Microsoft Sentinel with Defender XDR in the Microsoft Defender portal, ensure the following:
- A Log Analytics workspace with Microsoft Sentinel enabled.
- Microsoft Defender XDR data connector enabled in Microsoft Sentinel.
- Access to Microsoft Defender XDR within the Defender portal.
- Appropriate Azure roles for managing Microsoft Sentinel and Defender XDR features.
Technical Steps for Integration
Step 1: Onboarding Microsoft Sentinel
- Access the Microsoft Defender portal and sign into your account > https://security.microsoft.com
- In Microsoft Defender XDR and select Overview.

- Click Connect a workspace,
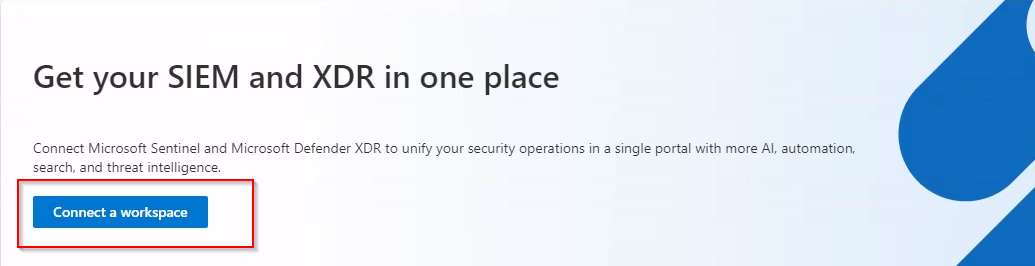
- Select your workspace, and then click Next.
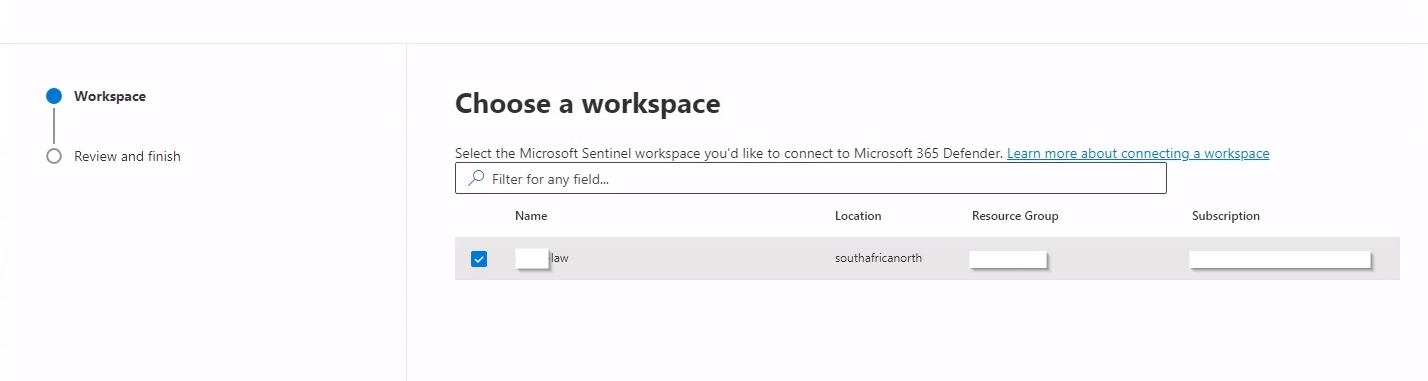
- Review and understand the product changes and implications of connecting your workspace.
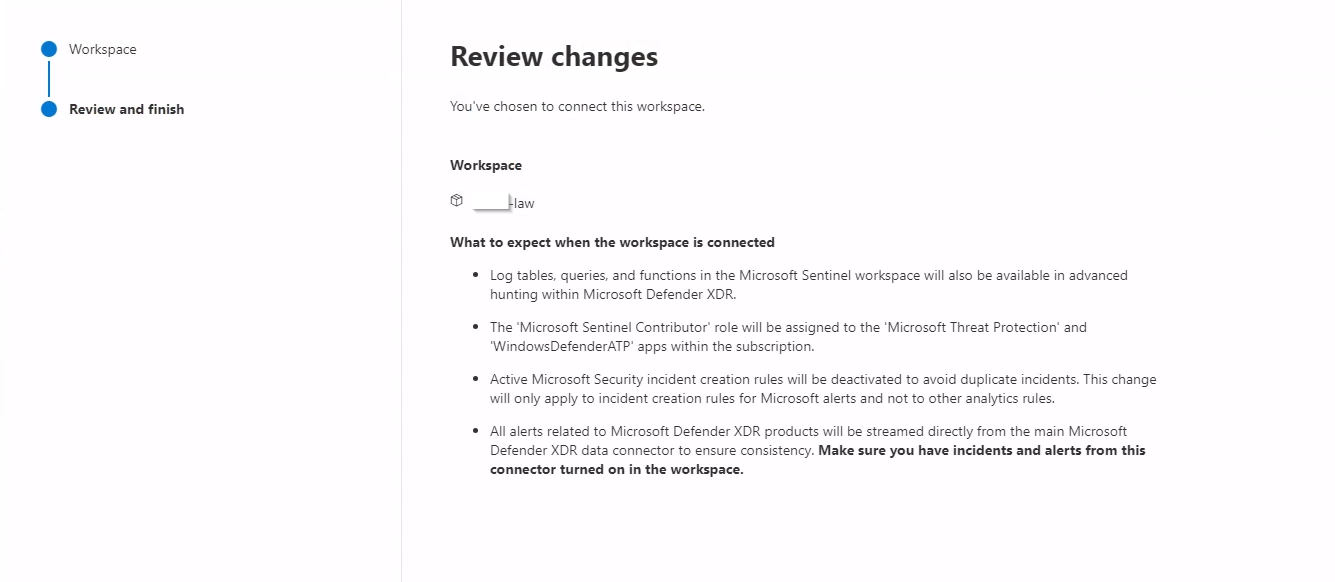
- Click Connect to finalize the integration.
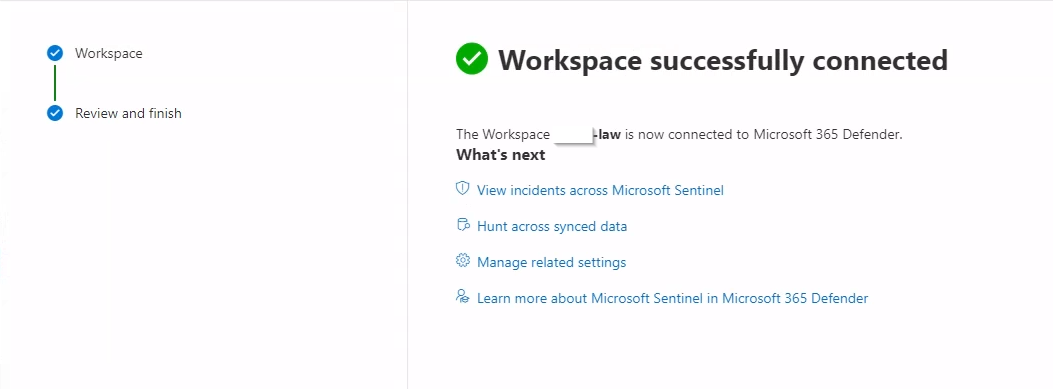
Step 2: Exploring Integrated Features
Once connected, Microsoft Sentinel will appear in the left-hand navigation pane of the Defender portal. This allows you to access unified features such as:
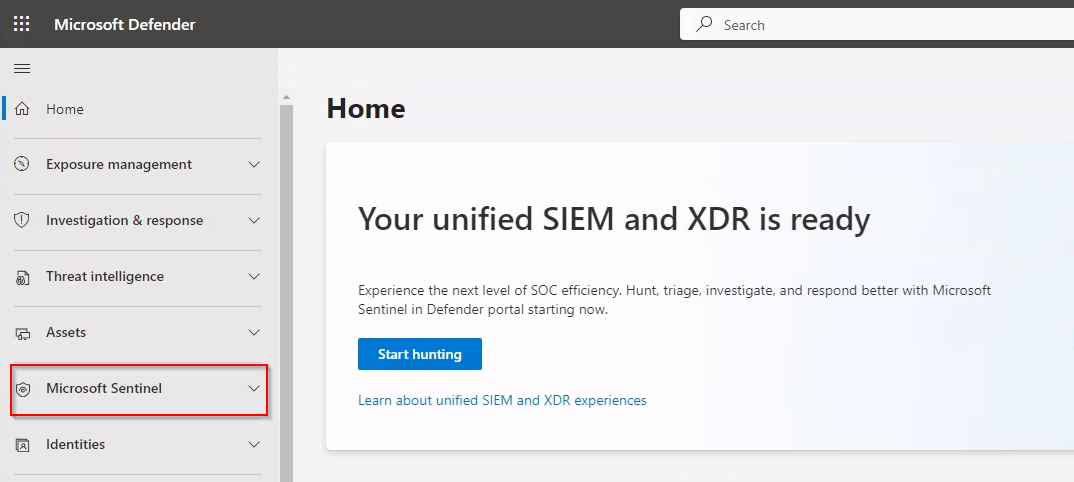
- Overview: Updated to show metrics from both Sentinel and Defender XDR.
- Incidents: Manage and investigate incidents sourced from a wide array of data.
- Advanced Hunting: Perform threat hunting using both Sentinel and Defender data.
Expanding Sentinel, you will be able to perform most of the Sentinel Activities as if you accessed it from the Azure Portal.
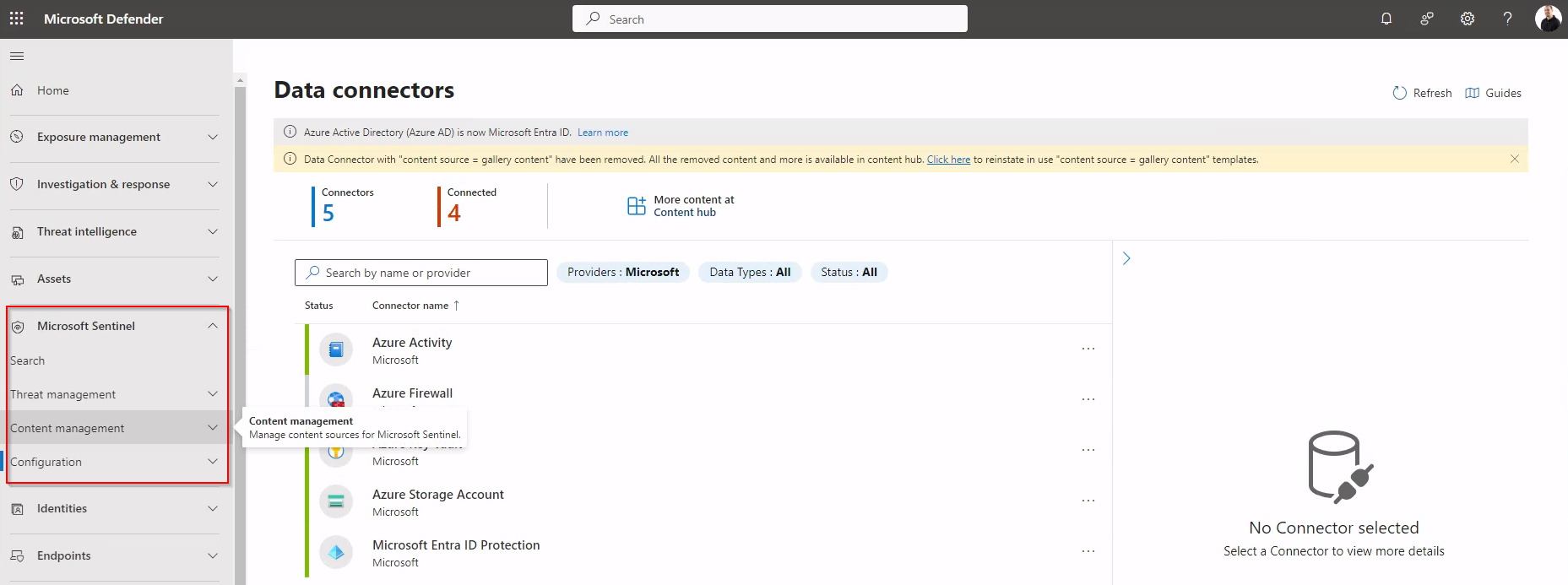
The new Unified portal also allows you to modify Microsoft Sentinel settings, to do this navigate to System > Settings
> Microsoft Sentinel.
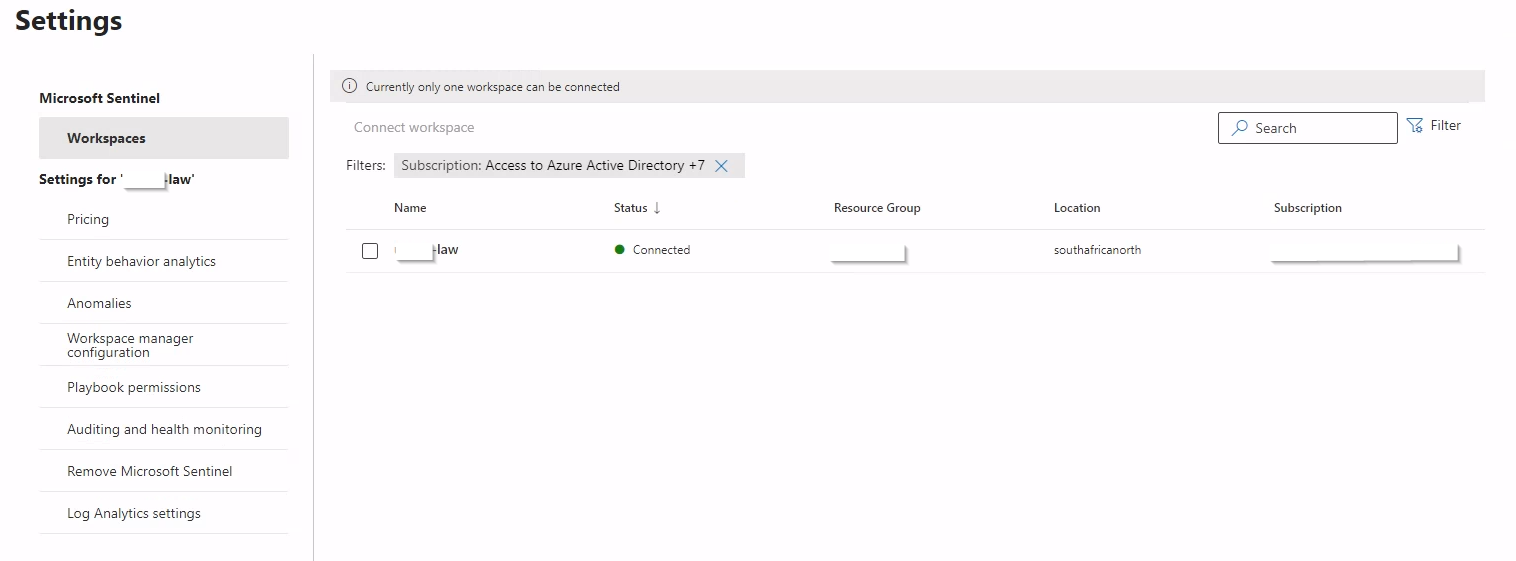
Let’s enable “Entity behaviour analytics’ using the new portal. > Entity behaviour analytics > Set UEBA
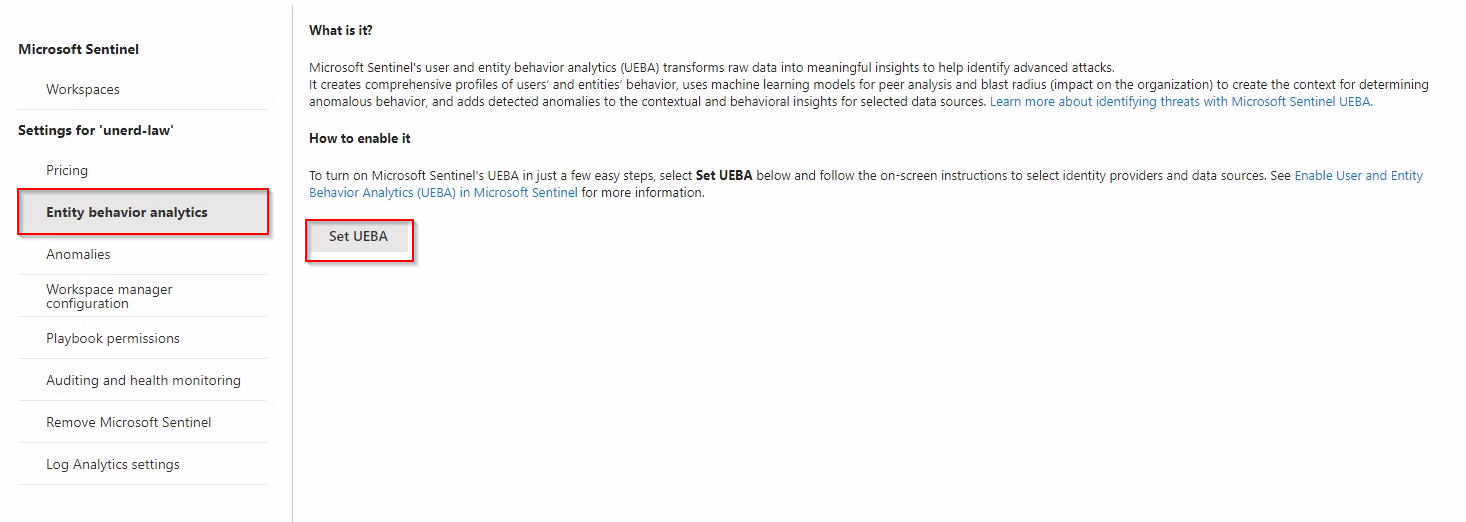
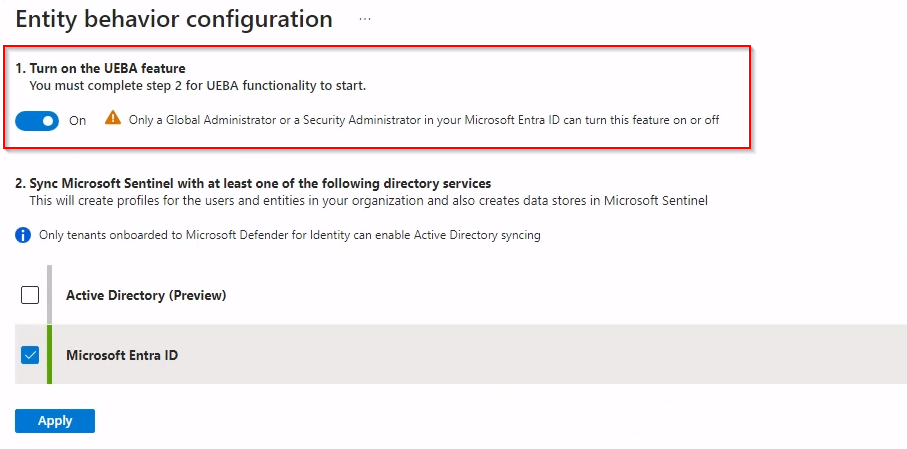
Enable “Turn on the UEBA feature”
Exploring Event Triggers: Analyzing How Events in Defender for Cloud Appear in Defender for XDR and Microsoft Sentinel Portals
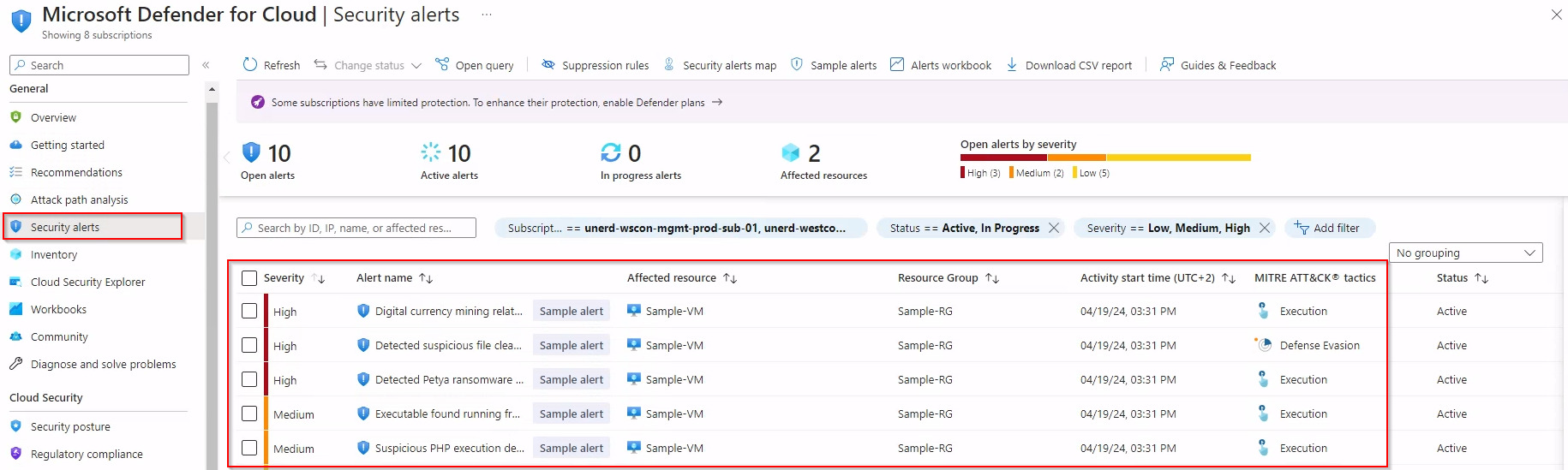
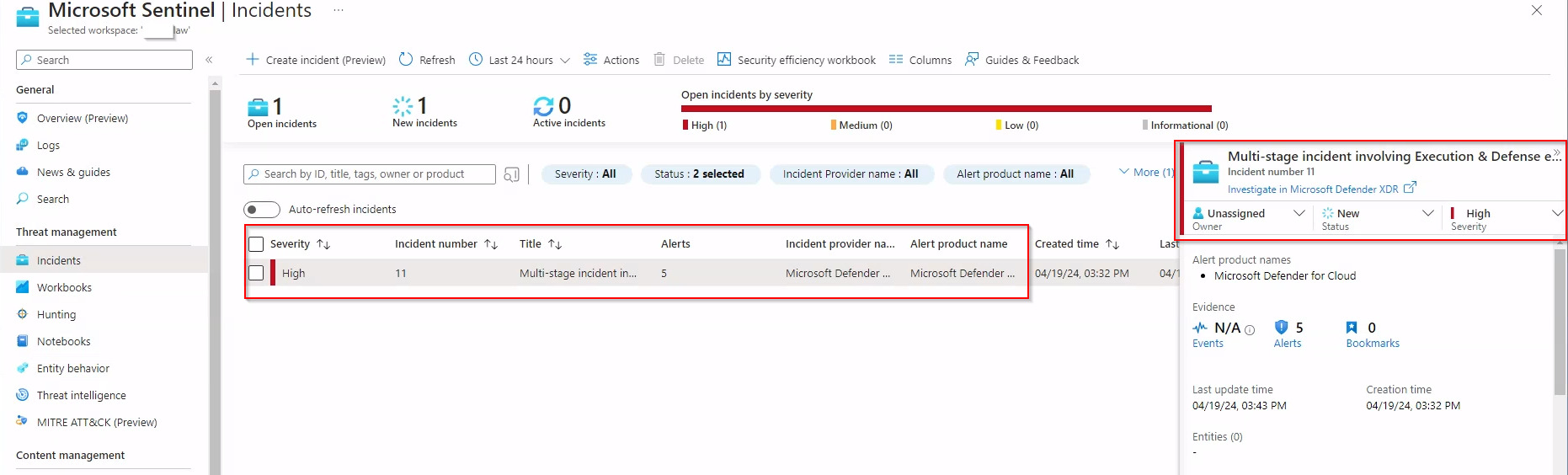
When events are triggered in Defender for Cloud, they become accessible not only within the Microsoft Defender XDR portal but across various security product portals, providing a holistic view of security threats. This cross-platform visibility is essential for security operations centers (SOCs), enabling them to track and respond to incidents more effectively. By having a unified display of events across different platforms, teams can leverage the integrated data to gain a deeper understanding of security alerts, streamline investigation processes, and enhance detection capabilities. This integration ensures that no matter where an event is initially detected, it is visible and manageable from any connected security portal, thus reinforcing the defense mechanism and ensuring a more robust security infrastructure.
Defender for Cloud Alerts
Microsoft Defender XDR Portal
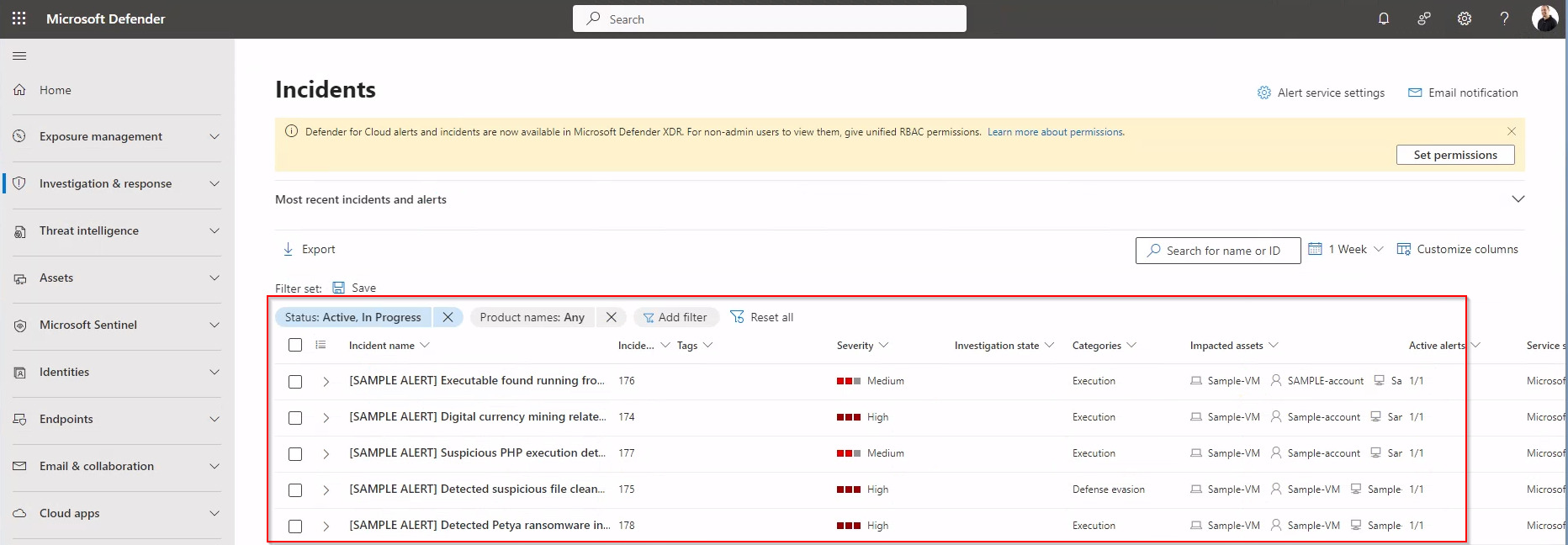
Microsoft Sentinel
Step 3: Offboarding (If Necessary)
To disconnect a workspace:
- Navigate to System > Settings > Microsoft Sentinel in the Defender portal.
- Select the connected workspace and click Disconnect workspace.
- Confirm your selection to remove the integration.
Conclusion
Integrating Microsoft Sentinel into the Microsoft Defender portal enhances the security operations platform by providing advanced threat detection, streamlined incident management, and reduced need for multiple tools. As this integration is still in preview, it’s essential to stay updated with Microsoft’s documentation and release notes for any changes or enhancements before the commercial release.
Key References for Further Reading
- Microsoft Sentinel in the Microsoft Defender portal
- Unified security operations platform with Microsoft Sentinel and Defender XDR
This integration signifies a major step forward in cybersecurity operations, combining powerful SIEM and XDR capabilities into a single, more effective system that enhances security incident response across the board.

Be First to Comment