Integrating Microsoft Sentinel, a cloud-native Security Information and Event Management (SIEM) system, with Defender for Cloud, provides organizations with an advanced security management and threat protection framework. Microsoft Sentinel offers an expansive view across the enterprise, delivering intelligent security analytics and threat intelligence, making it easier for businesses to detect, investigate, and respond to cybersecurity threats. Meanwhile, Defender for Cloud offers in-depth security posture management and threat protection services for cloud environments. But, does integrating Sentinel with Defender for Cloud eliminate the need for the continuous export of logs to a Log Analytics workspace? Let’s delve deeper.
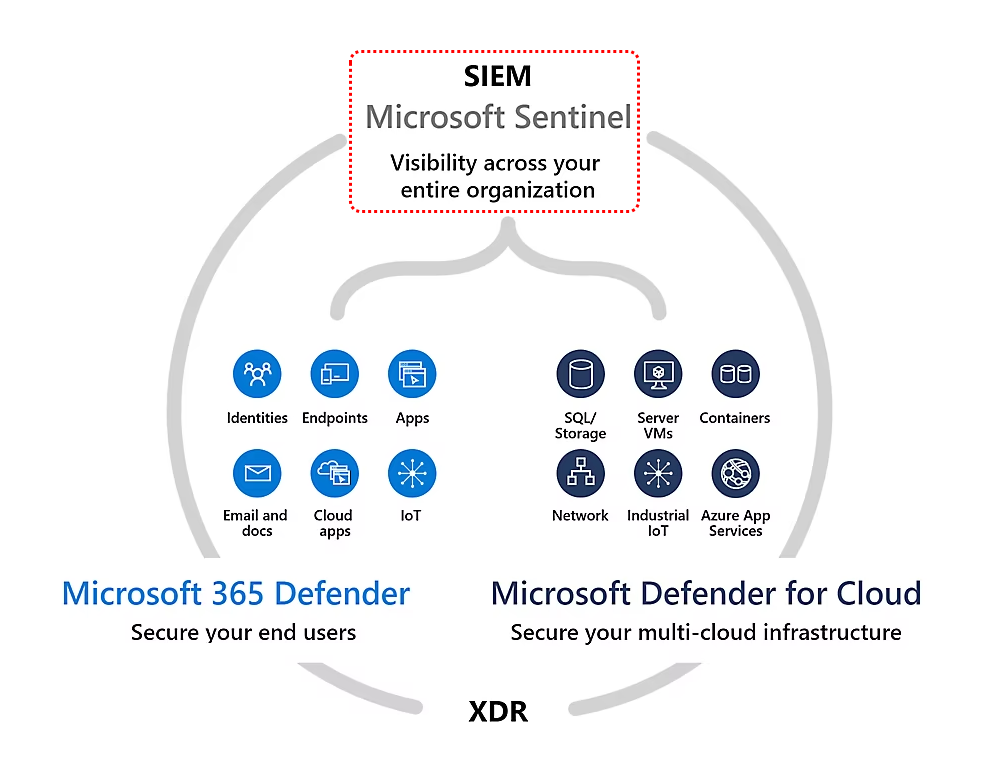
Understanding the Integration
Microsoft Sentinel seamlessly integrates with Defender for Cloud, pulling in security alerts and recommendations directly. This direct pipeline is designed to streamline the ingestion process, making it unnecessary to configure continuous export for exporting Defender for Cloud’s data into a Log Analytics workspace for Sentinel’s consumption. This integration signifies a shift towards a more efficient method of managing security alerts and recommendations.
When Might Continuous Export Still Be Relevant?
Despite the direct integration offering a streamlined approach, there are scenarios where continuous export to a Log Analytics workspace might still be beneficial:
Detailed Log Analysis
If your security operations or compliance requirements necessitate detailed logging information or non-alert data types (e.g., security posture data, regulatory compliance information) from Defender for Cloud, continuous export remains a viable solution. This data supports in-depth analysis and insight generation beyond the scope of security alerts.
Custom Queries and Workbooks
Organizations often develop custom queries, workbooks, or dashboards that operate on detailed log data exported from Defender for Cloud. Maintaining continuous export supports these customizations, enabling security teams to leverage tailored insights for decision-making.
Data Retention and Compliance
Depending on an organization’s data retention policies and regulatory compliance requirements, continuous export to a Log Analytics workspace might be necessary to ensure all relevant data is appropriately stored and accessible for the required duration.
How to configure Continuous export in Defender for Cloud: Guide Here
The Value Proposition of Microsoft Sentinel
Choosing Microsoft Sentinel as your SIEM solution offers numerous advantages:
- Comprehensive Security Analysis: Sentinel’s broad integrations across cloud environments and applications enable a unified view of security threats and vulnerabilities, enhancing detection and response capabilities.
- Efficient and Cost-effective: By reducing the need for continuous data export and storage in separate workspaces, Sentinel can help streamline operations and reduce costs associated with data management and storage.
- Advanced Threat Intelligence: Leveraging artificial intelligence and machine learning, Sentinel provides cutting-edge threat detection, helping to identify and mitigate threats faster and more accurately.
- Automation and Orchestration: Sentinel’s automated response capabilities allow for rapid containment and remediation of threats, reducing the time and effort required for manual interventions.
Conclusion
While the direct integration of Microsoft Sentinel with Defender for Cloud streamlines the security management process, the need for continuous export to a Log Analytics workspace may still arise based on specific organizational needs. Detailed log analysis, custom analytics, and compliance requirements are key factors that might necessitate maintaining continuous export. However, the efficiency, cost-effectiveness, and advanced capabilities of Microsoft Sentinel highlight its value as a leading SIEM solution, capable of transforming how organizations approach their cybersecurity defense posture.
By evaluating the specific requirements and benefits in the context of your organization’s security and compliance landscape, you can make an informed decision on the optimal configuration and integration of these powerful security tools.

Be First to Comment