Enable MFA for All Office 365 Users using Azure Active Directory Identity Protection.
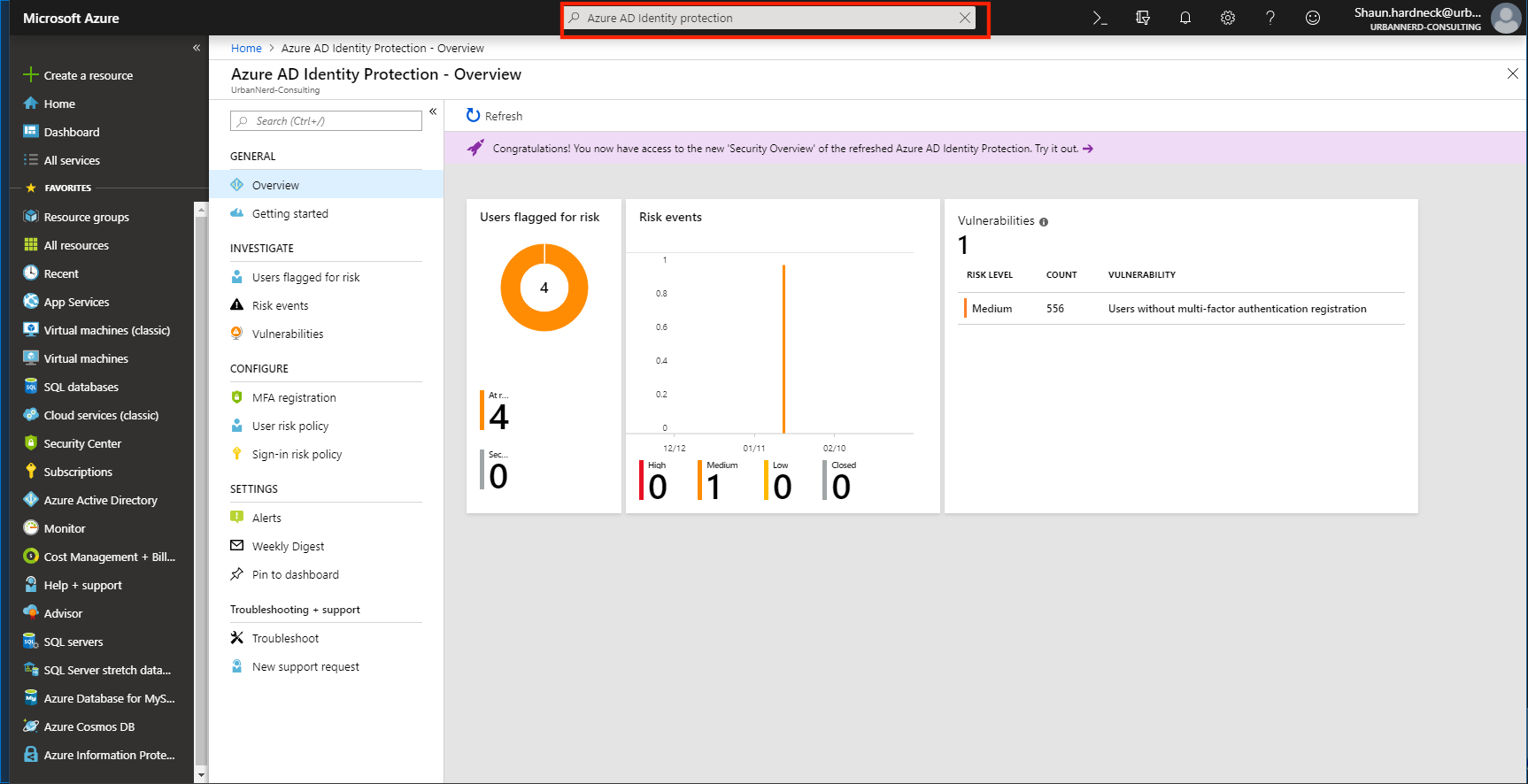
“Azure Active Directory Identity Protection provides a consolidated view of at risk users, risk events and vulnerabilities, with the ability to remediate risk immediately, and set policies to auto-remediate future events. The service is built on Microsoft’s experience protecting consumer identities and gains tremendous accuracy from the signal from over 13B logins a day.”
To get started you will have to login to Office 365 Admin Portal https://Portal.Office.com
From the Admin console, open Azure Active Directory.
From the Azure Active Directory Portal, click on the search and type MarketPlace.
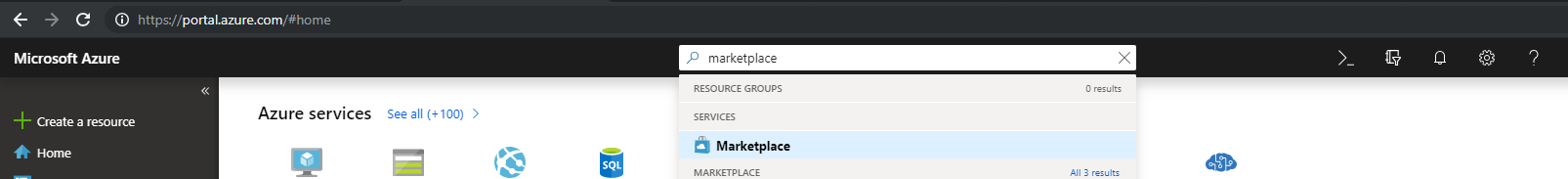
From the MarketPlace in the Everything search bar type: Azure AD Identity Protection.
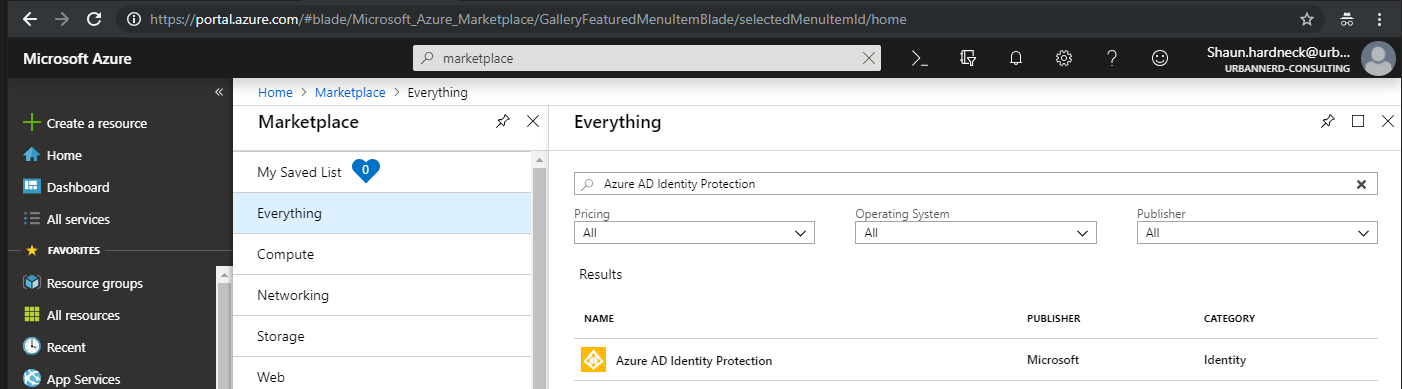
Click on Azure AD Identity Protection then on the right-hand side click on Create.
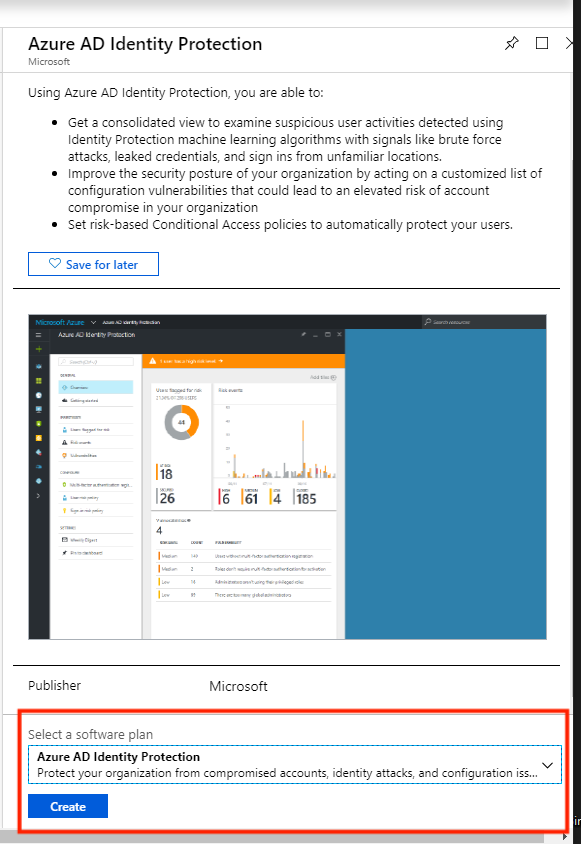
Before completing the creation, you will be moved to a secondary window to select your Directory. Select the directory and click create.

To get to Azure AD Identity protection portal, click on the search on top of the Azure portal and type Azure AD Identity Protection.
The next step is to configure which users we want to enable MFA. For the purpose of this demo I will select a security group.
To get started, click on the MFA registration under CONFIGURE and then select Assignments.

From the Assignments Menu, select “include” and then select “select individuals and groups”, Select the group who needs to have MFA enabled and click select at the bottom of the page.

Click on Done at the next blade.

Next you will be redirected back to the beginning and then select Controls.
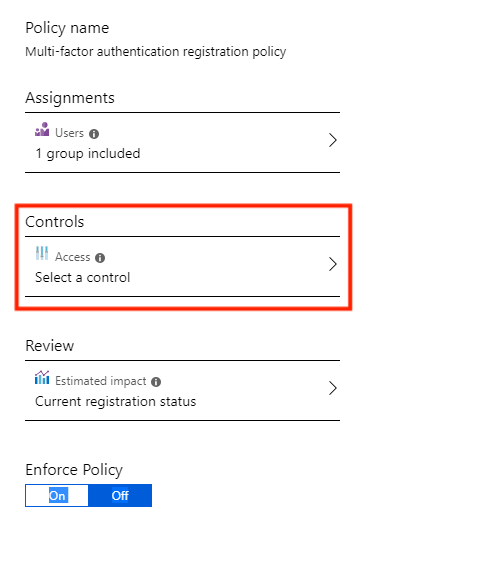
Then make sure MFA is selected and then click on Select.

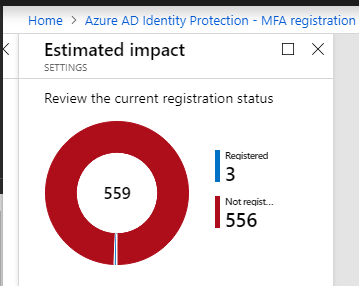
Next you can view what the impact of your change will be and how many users will be affected, so because I have selected a Security group on 3 users will be impacted.
To complete the process, click on “Enforce Policy” and then click on Save at the bottom of the blade.
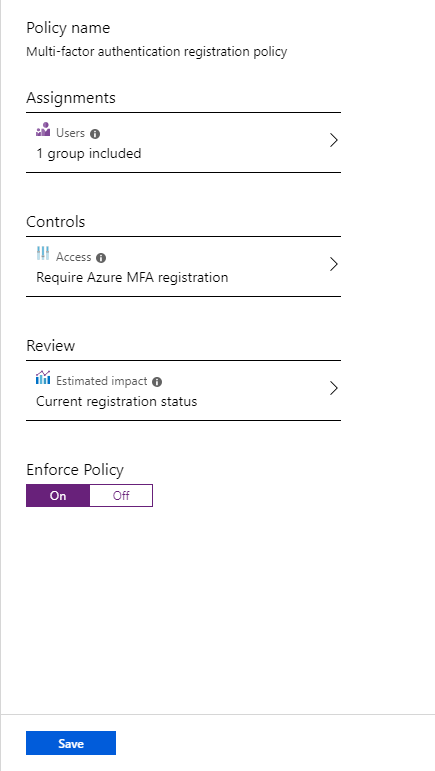
And this is how you can enable MFA for all users or selected users in your Organization without having to enable it for individual users


Be First to Comment