Protect your Office 365 Tenant with Azure AD Risky Sign-Ins
Microsoft Office 365 and Azure Active Directory provides some very Powerful tools related to security. These tools are what I call the CLOUD GEMS. (pot of gold under the rainbow) They are very useful when it comes to finding compromised accounts within your Office 365 tenant.
Azure AD detects suspicious actions that are related to your user accounts. For each detected action, a record called risk event is created. For more details, see Azure Active Directory risk events.
The detected risk events are used to calculate:
- Risky sign-ins – A risky sign-in is an indicator for a sign-in attempt that might have been performed by someone who is not the legitimate owner of a user account. For more details, see Risky sign-ins.
- Users flagged for risk – A risky user is an indicator for a user account that might have been compromised. For more details, see Users flagged for risk.
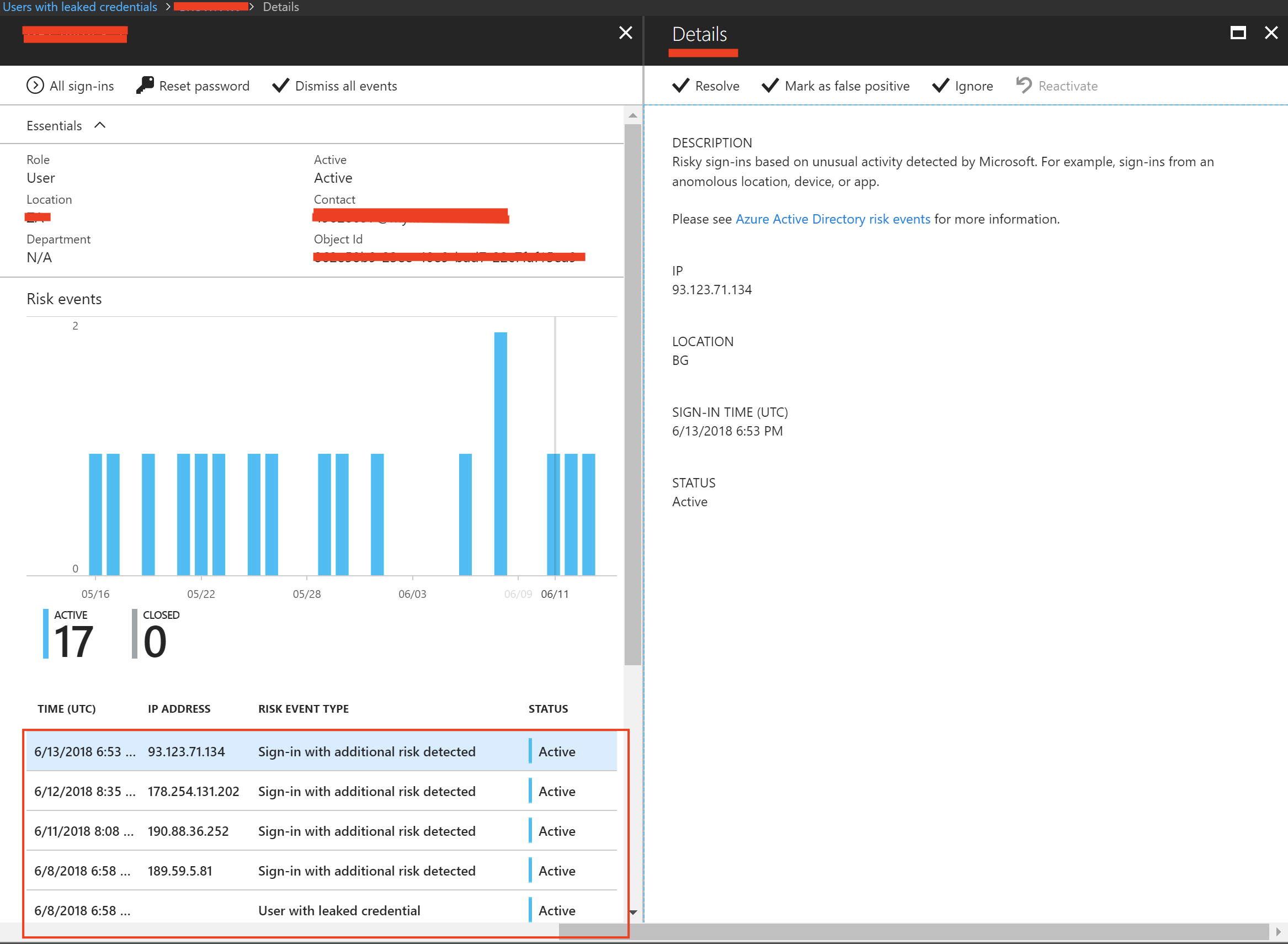
What does Leaked Credentials mean?
Account usernames and passwords that have been posted online by attackers. Microsoft collects this data from researchers, industry partners, and law enforcement agencies.
SECURITY IMPACT
Leaked sign-in credentials are traded on the black market and can easily land in the hands of a malicious entity, intent on attacking the user or organization.
How do you find the this information?
Navigate to https://portal.azure.com, then click on Azure Active Directory.
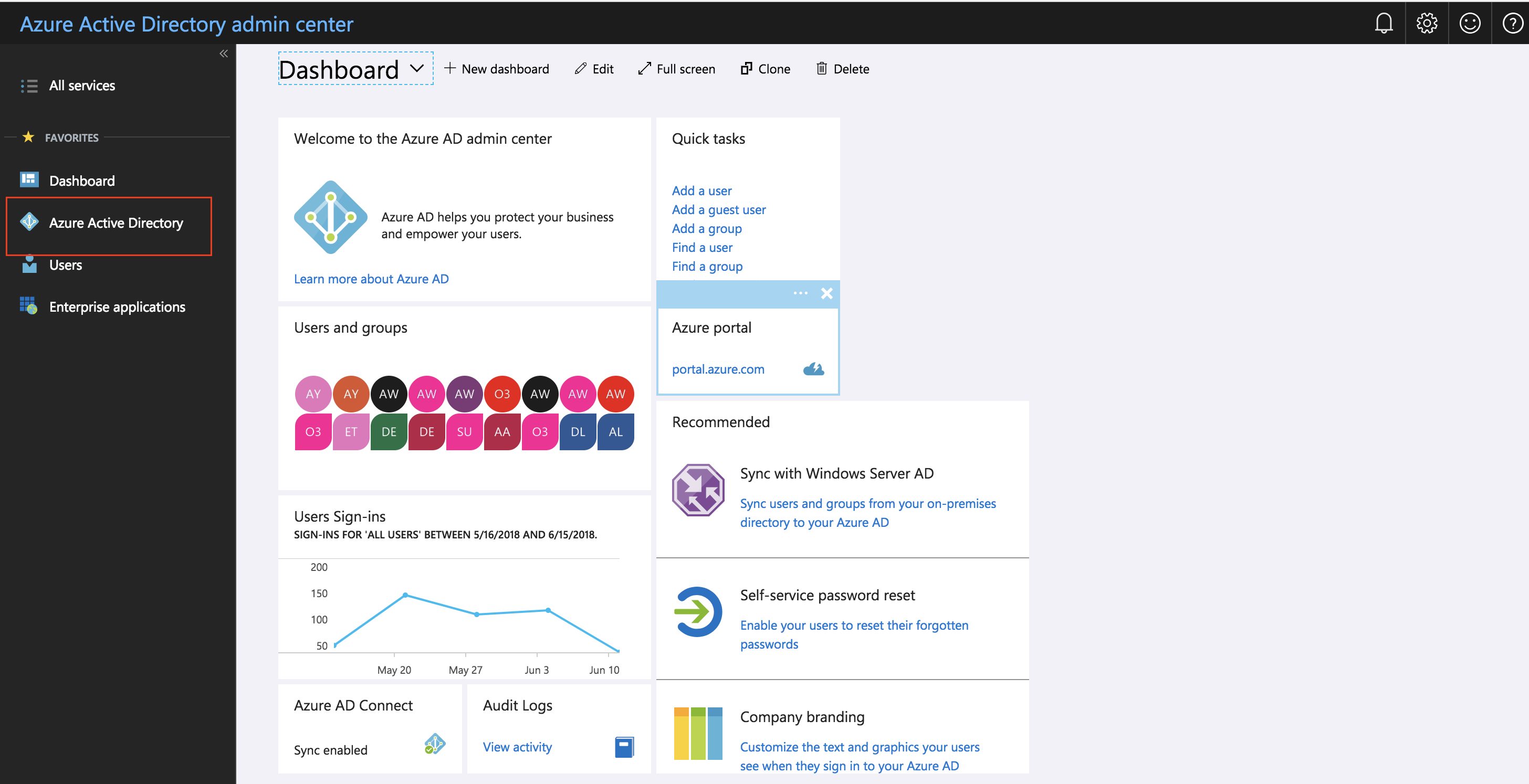
From the Azure Active Directory Menu, scroll down until you see the option Risky Sign-In.
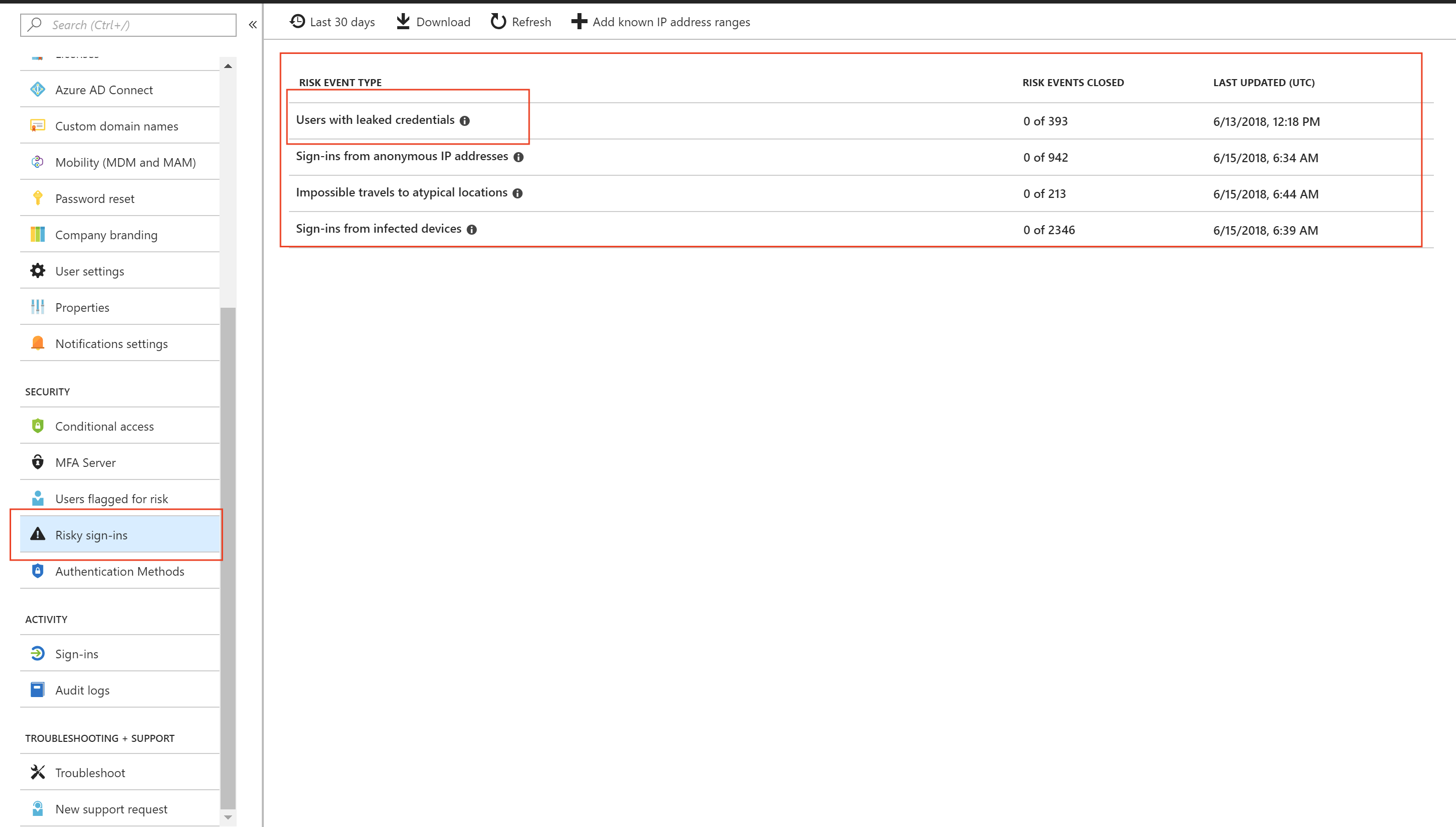
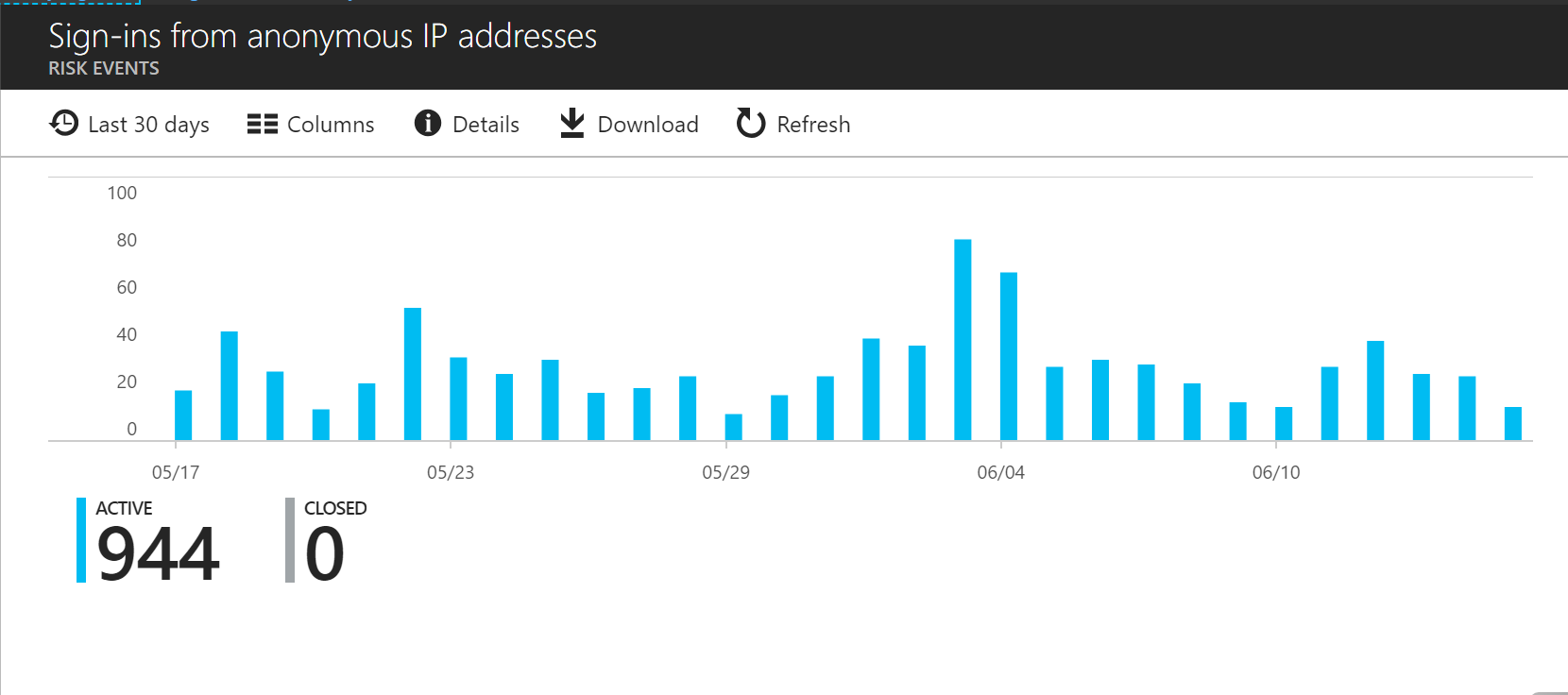
From the Risky Sign-In, you will notice on the right hand side that your current risks will be listed there.
As mentioned above about what the Users with leaked credentials mean, here is what Sign-In from anonymous IP addresses mean.
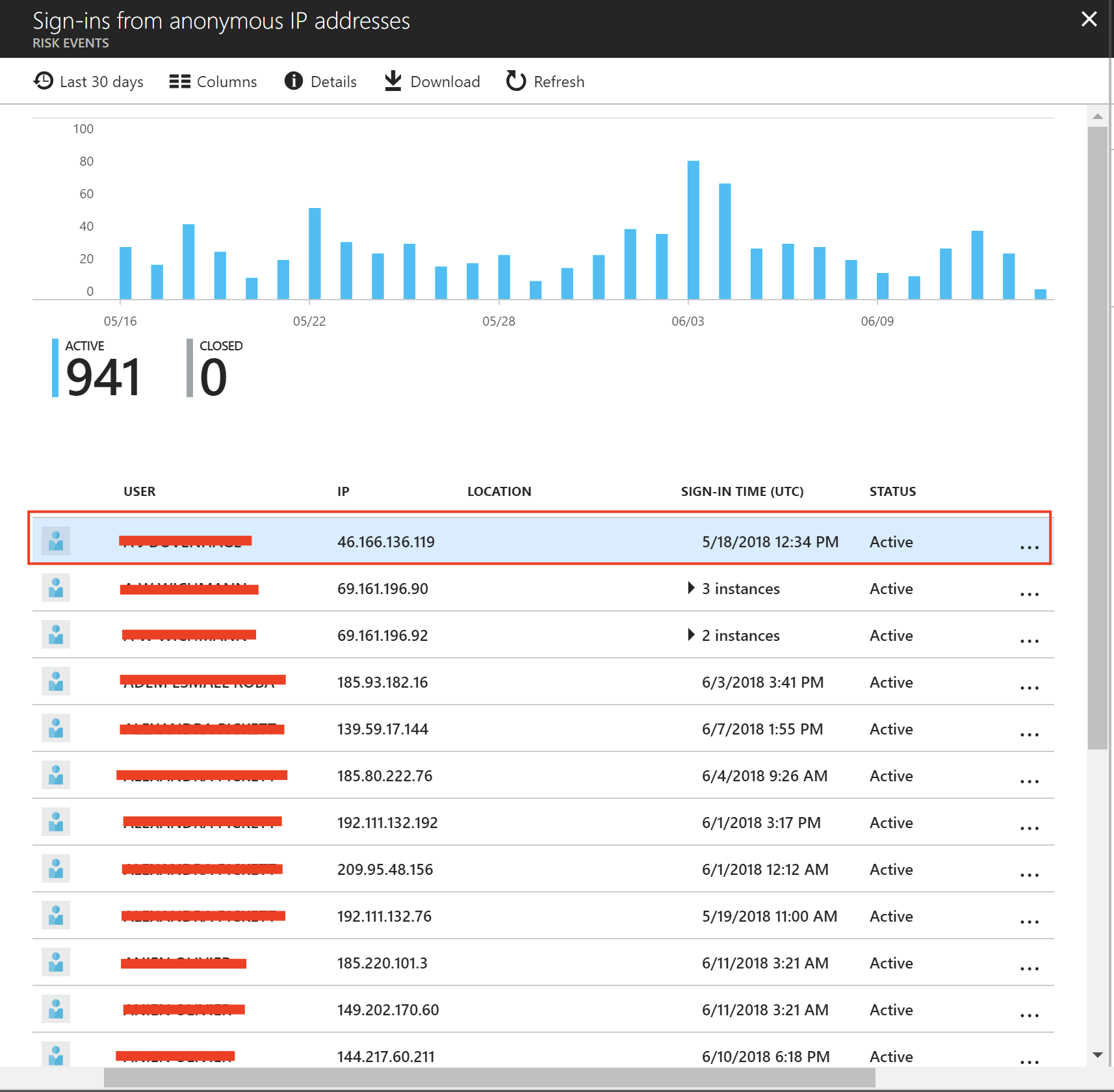
What does Sign-Ins from anonymous IP addresses mean?
Sign-ins from IP addresses that are anonymous, such as Tor IP addresses.
SECURITY IMPACT
This risk event may indicate that an attacker has compromised the user’s credential and is exploiting it through an anonymous IP address.
The below example, we can see that an anonymous IP address was used to access the users profile and that the originating IP was traced from a country that the users has not travelled to.

What Azure AD license do you need to access a security report?
All editions of Azure Active Directory provide you with risky sign-ins reports.
However, the level of report granularity varies between the editions:
- In the Azure Active Directory Free and Basic editions, you already get a list of risky sign-ins.
- The Azure Active Directory Premium 1 edition extends this model by also enabling you to examine some of the underlying risk events that have been detected for each report.
- The Azure Active Directory Premium 2 edition provides you with the most detailed information about all underlying risk events and it also enables you to configure security policies that automatically respond to configured risk levels.
These are just a few of the little hidden pots of gold that is provided by Microsoft for all the Cloud customers to help them protect their environments and end users.


Hi there, all the time i used to check website posts here early in the morning,
since i love to learn more and more.