Getting Started with Microsoft Security Copilot
What is Microsoft Security Copilot?
Microsoft Security Copilot is an innovative generative AI security tool designed to help organizations protect themselves from cyber threats. By combining AI-powered capabilities with Microsoft’s extensive security ecosystem, Security Copilot enables IT and security professionals to detect and respond to threats, process security signals, and assess risk exposure with unprecedented speed and scale.
In simpler terms, Security Copilot acts as your AI-powered security assistant, helping your organization make faster, smarter security decisions while reducing operational complexities.
This is the first in a series of blog posts dedicated to helping you master Microsoft Security Copilot. In this post, we’ll cover everything you need to get started with Copilot for Security. Let’s go, Pilots!
For customers looking to test Microsoft Security Copilot, it is possible to start with a single Security Compute Unit (SCU). However, this configuration is not recommended for production environments, as it may limit performance and scalability.
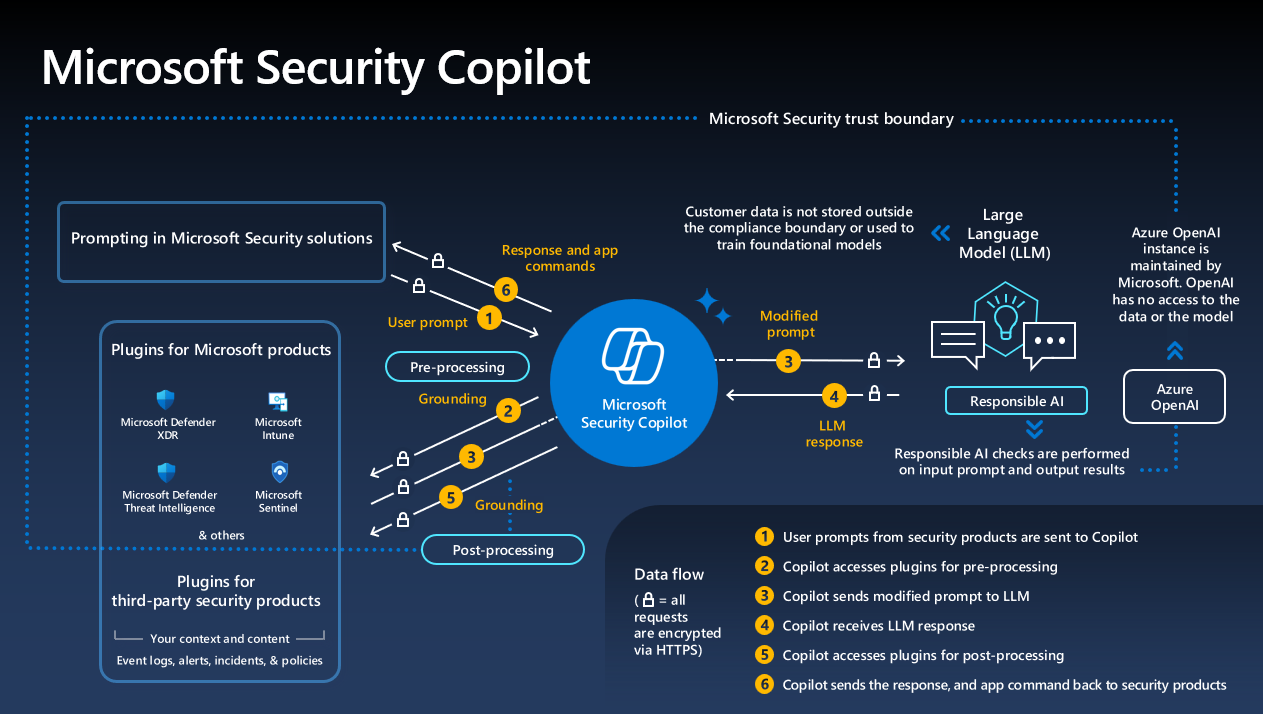
Applying Zero Trust Principles to Microsoft Security Copilot
Zero Trust is a critical security framework that helps organizations strengthen their defenses by assuming breach and verifying every access attempt. Microsoft Security Copilot is designed to align with Zero Trust principles, providing organizations with advanced capabilities to mitigate risks and enhance their security posture.
Why Zero Trust is Essential for Security Copilot
- Assume Breach: Security Copilot operates on the principle that no access or activity should be trusted implicitly. By integrating with Zero Trust policies, Copilot ensures that all signals and responses are validated against your organization’s security framework.
- Least Privilege Access: Roles and access controls in Security Copilot should be configured to grant users the minimum permissions necessary, reducing exposure to threats.
- Visibility and Insights: Copilot’s integration with other Microsoft security services provides detailed visibility into incidents, enabling faster and more informed decision-making.
To learn more about Zero Trust and how it applies to Security Copilot, refer to the Zero Trust Principles for Security Copilot.
Minimum Requirements
Subscription
- You need an active Azure subscription to purchase Security Compute Units (SCUs).
Create your free Azure account if you don’t already have one.
Security Compute Units (SCUs)
SCUs are the required units of resources for dependable and consistent performance of Microsoft Security Copilot. It is essential to understand the billing and provisioning model to avoid confusion.
Key Billing Details
- Provisioned Capacity Model: Security Copilot is sold in a provisioned capacity model and billed by the hour.
- Hourly Blocks: SCUs are billed in full hourly increments. Any usage within the hour is charged as a full SCU, regardless of the start or end time.
Example:
-
- If an SCU is provisioned at 9:05 AM and deprovisioned at 9:35 AM, you will still be charged for the full hour (9:00 AM to 10:00 AM).
- Similarly, if you provision another SCU at 9:45 AM, it will count as a second unit for the same hour.
Best Practice for Provisioning
To maximize cost efficiency, make SCU provisioning changes at the beginning of the hour.
Provisioning Recommendations
- Start with a minimum of 3 SCUs for basic exploration.
- For testing purposes, you can provision 1 SCU, but this is not recommended for production environments due to potential performance limitations.
- The maximum limit is 100 SCUs.
Onboarding to Security Copilot
Getting started with Microsoft Security Copilot involves setting up the necessary resources and configuring your environment to ensure smooth and secure operation. Onboarding ensures that your organization is ready to leverage the full capabilities of Security Copilot, including access to advanced AI-powered tools and seamless integration with your existing Microsoft security infrastructure.
This process includes provisioning capacity, which ensures you have the required Security Compute Units (SCUs) to run Security Copilot, and configuring the default environment, which determines data residency, sharing preferences, and role assignments. Proper onboarding lays the foundation for utilizing Security Copilot effectively while aligning with your organization’s security and compliance requirements.
Onboarding involves two key steps:
Step 1: Provision Capacity
Option 1 (Recommended): Through Security Copilot
- Navigate to Security Copilot Portal and sign in.
- Select Get Started.
After selecting getting started, wait a few minutes you will see the following screen.
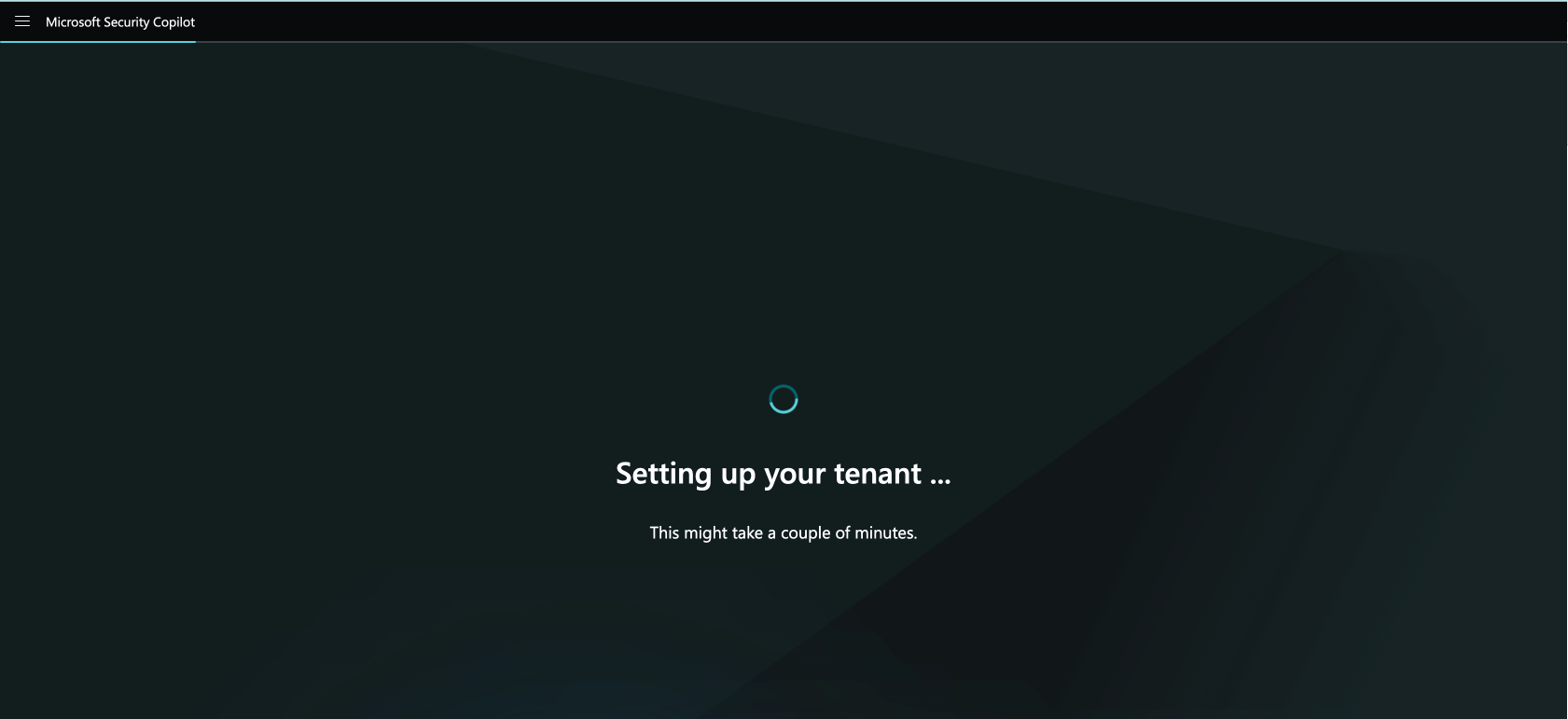
- Set Up Security Capacity:
- Choose an Azure subscription.
- Associate the capacity with a resource group.
- Provide a name for the capacity.
- Select the prompt evaluation location.
-
- Specify the number of SCUs.
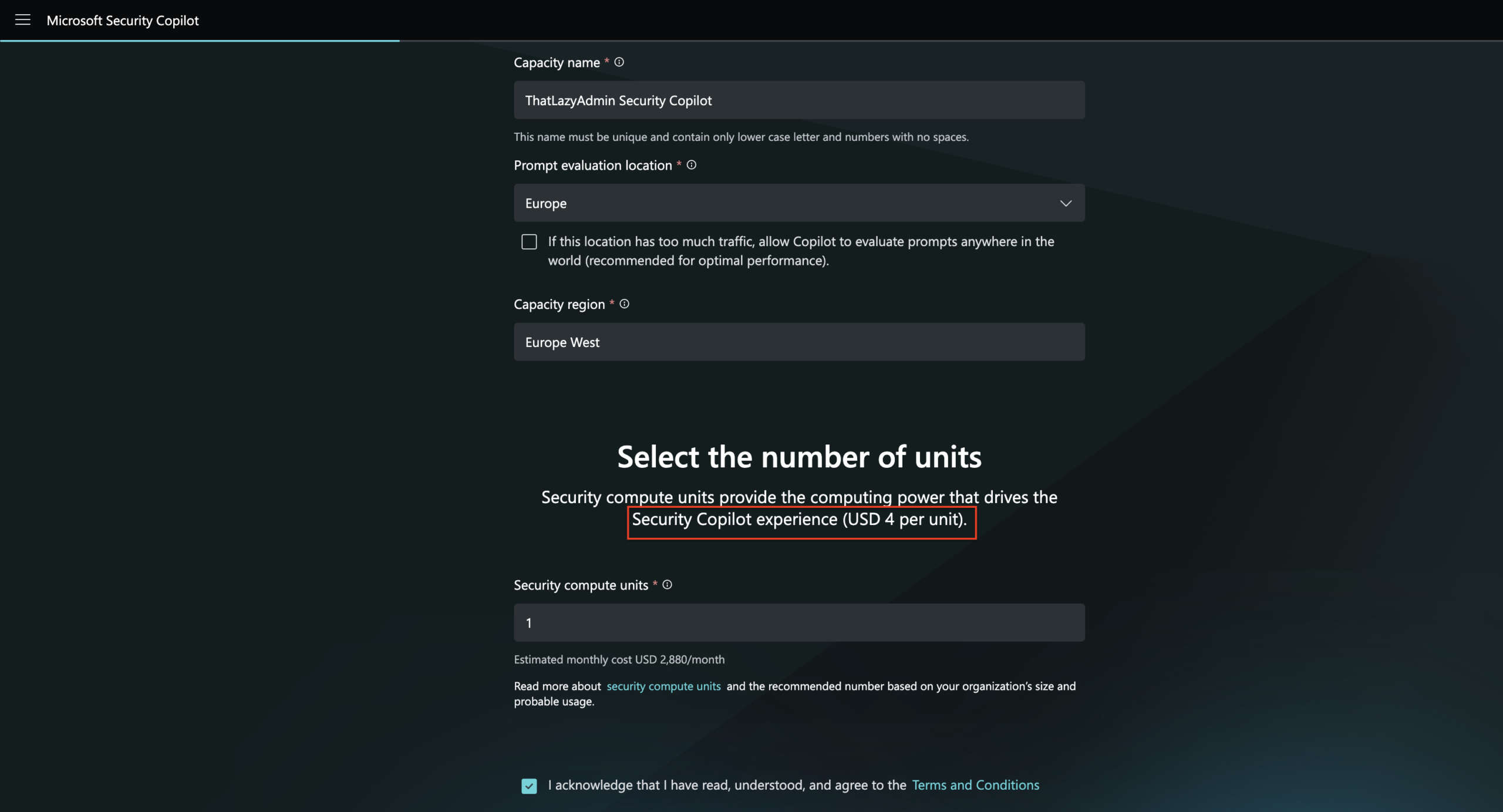
- Acknowledge terms and conditions and select Continue.
- The capacity setup will take a few minutes. A confirmation screen will appear once completed.
Click next in the bottom right hand-side.
On the next screen, you’ll have the option to participate in enhancing Security Copilot by choosing what types of data Copilot can collect and share with Microsoft. This allows you to contribute to improving the platform while maintaining control over your data preferences.
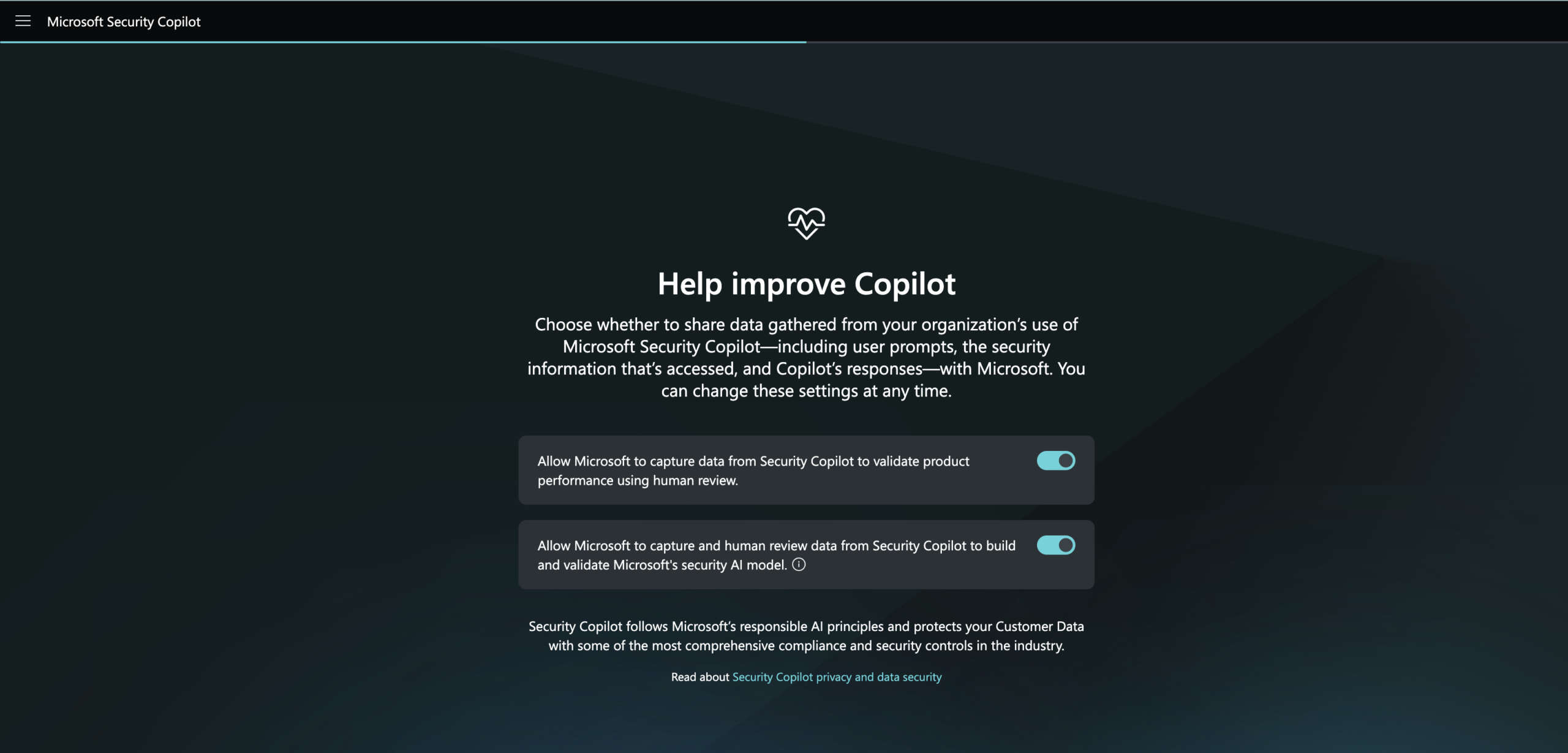
Click Continue on the next screen.
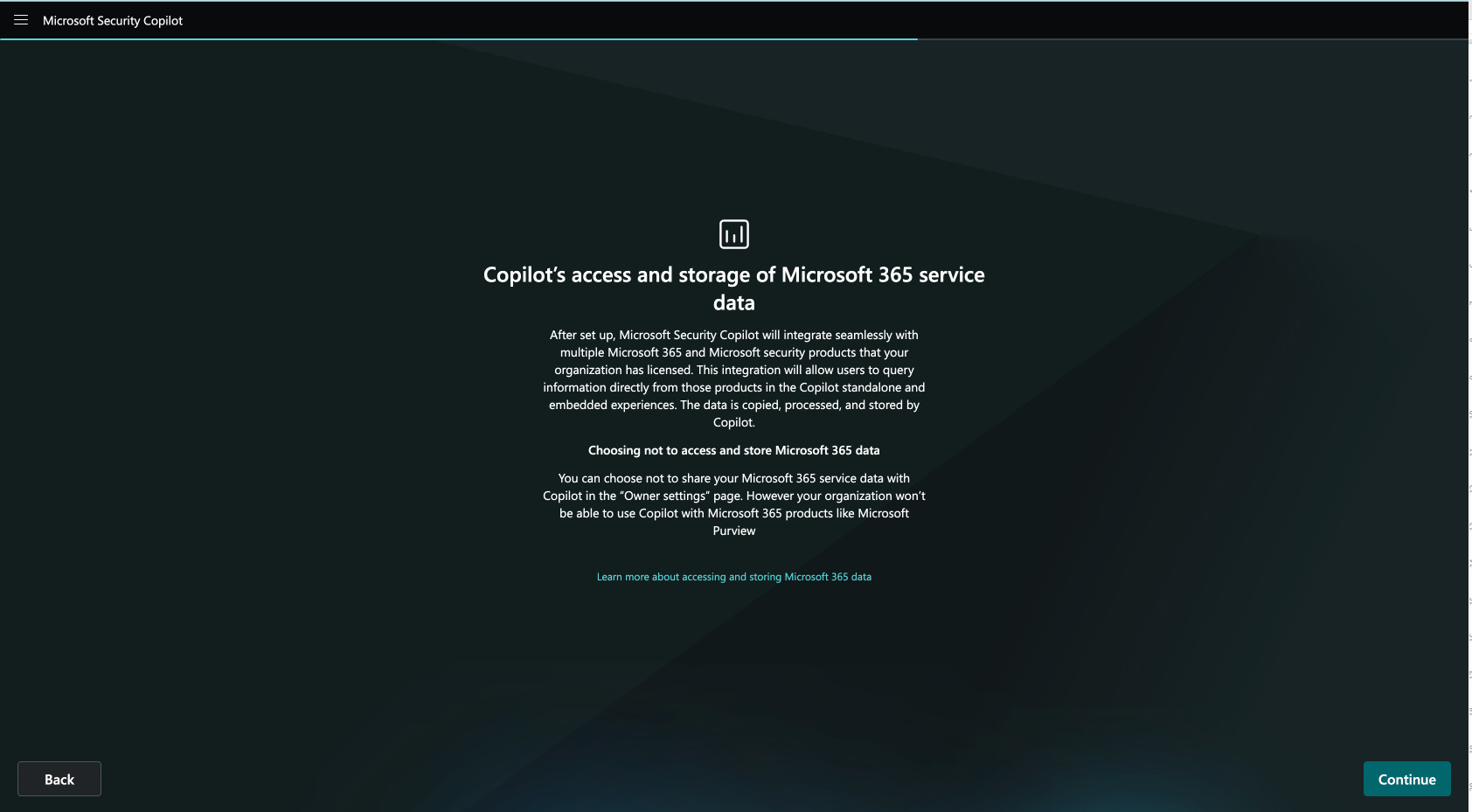
This image highlights how Security Copilot uses Microsoft Purview to log audit data, including admin and user actions, while ensuring data is stored in compliance with Microsoft 365’s regional data residency policies. You can select “Allow Microsoft Purview to access, process, copy, and store Customer Data from your Security Copilot service.
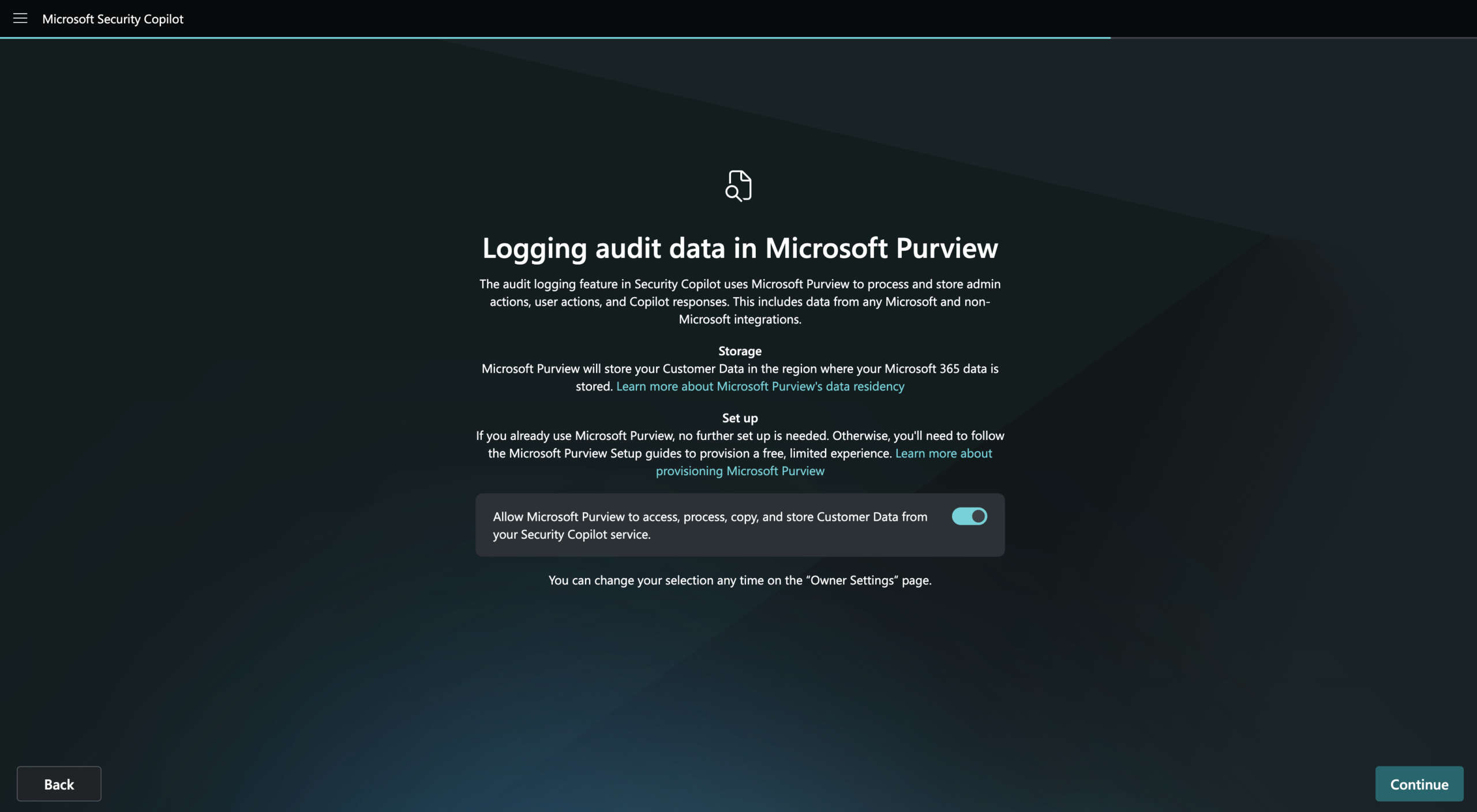
During the Microsoft Security Copilot setup, you can assign access to contributors and owners by selecting the Recommended Microsoft Security Roles. This option simplifies access management by granting predefined roles like Global Administrator and Security Administrator access to Copilot. Contributors gain access to Copilot responses based on their existing permissions within Microsoft Security products, while owners have full control over settings, plugin management, and role assignments. You can also choose to defer adding roles and configure them later via the role assignment page.
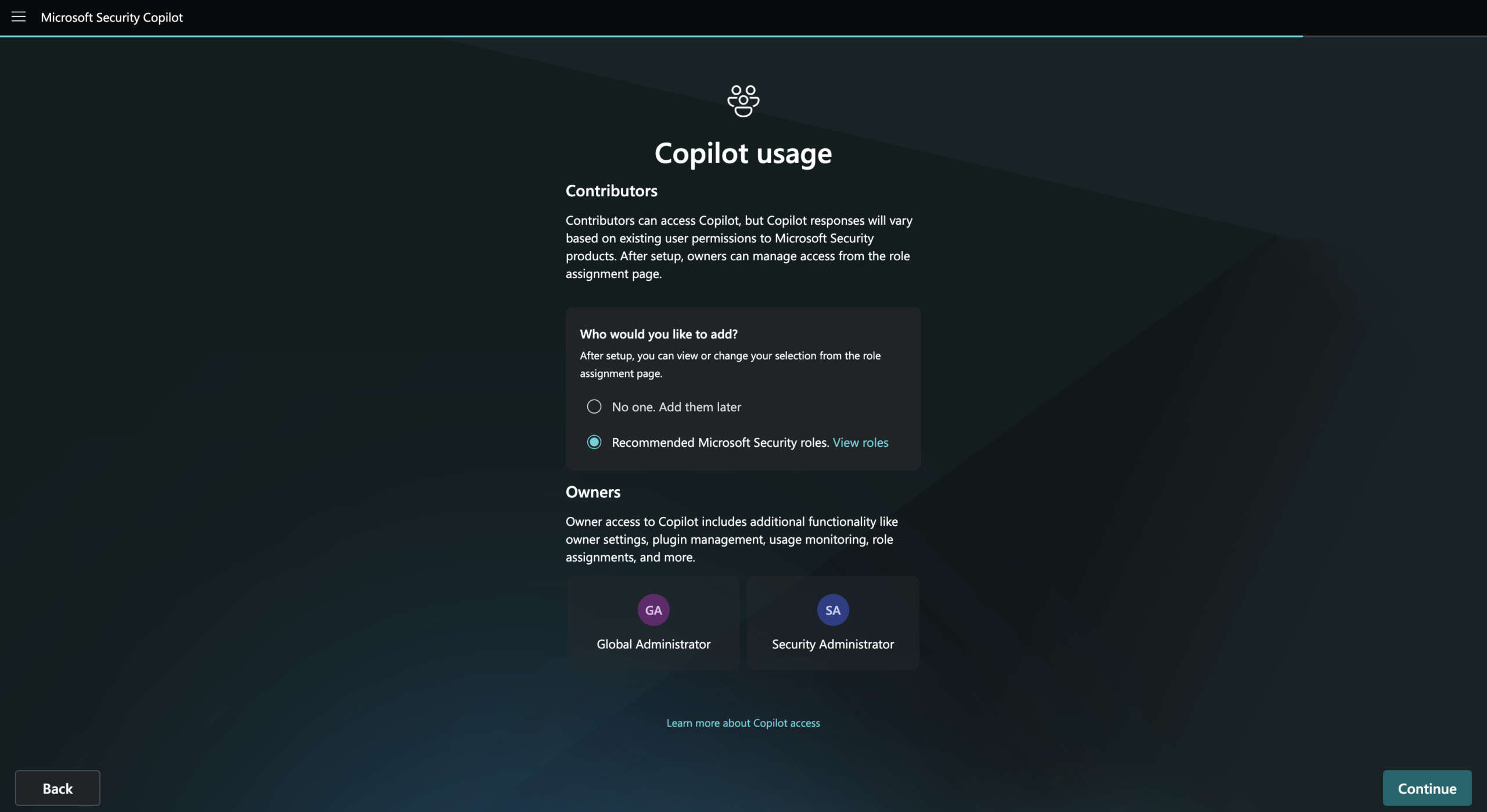
Finaly screen of happiness, Security Copilot setup completed and now can now share the Url with your colleagues.
Your Microsoft Security Copilot Home screen will look as follow after your setup has been completed.
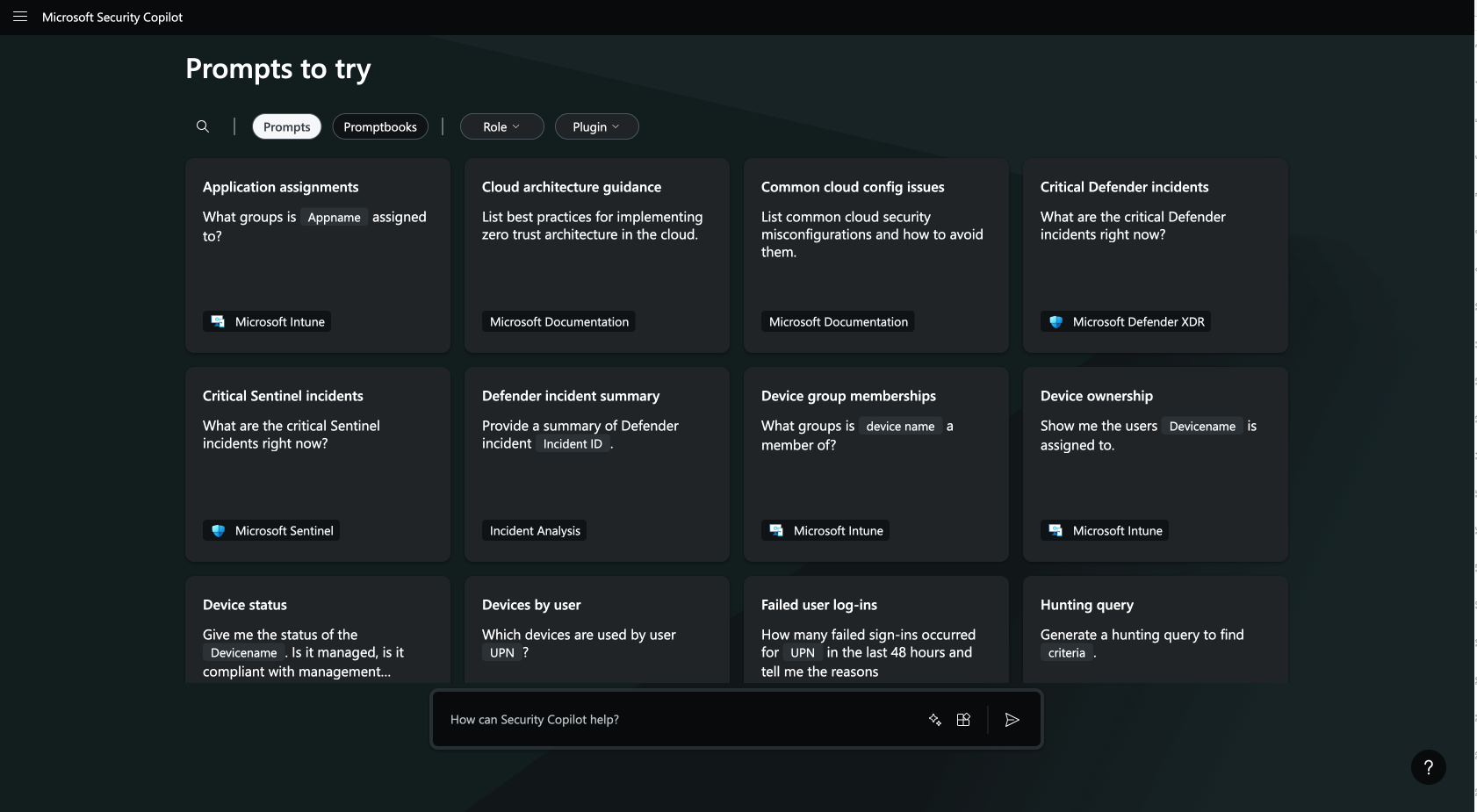
Option 2: Through Azure Portal
- Sign in to Azure Portal.
- Search for Security Copilot and select it from the list of services.
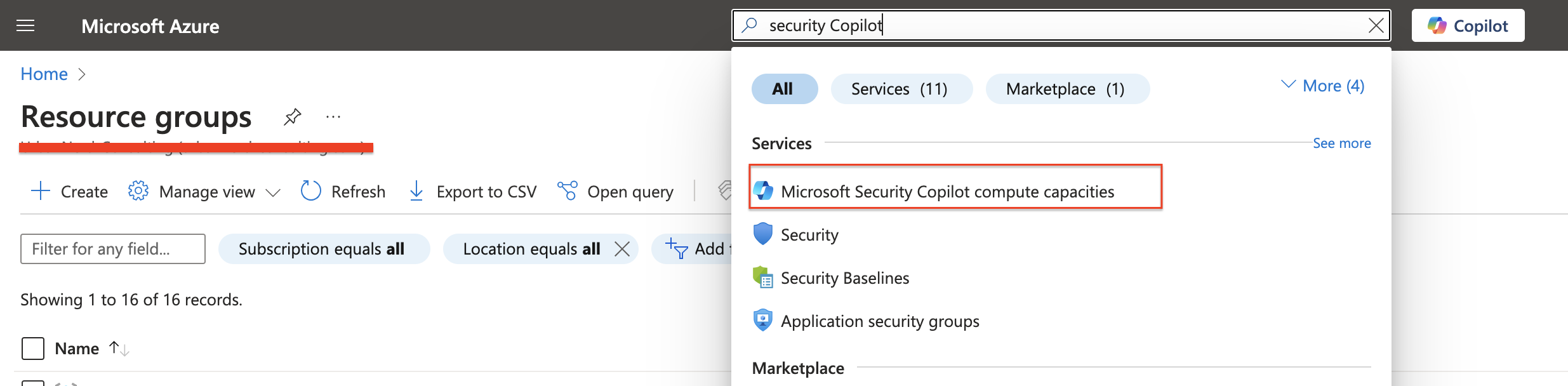
Click “Create Microsoft Security copilot compute capacity”
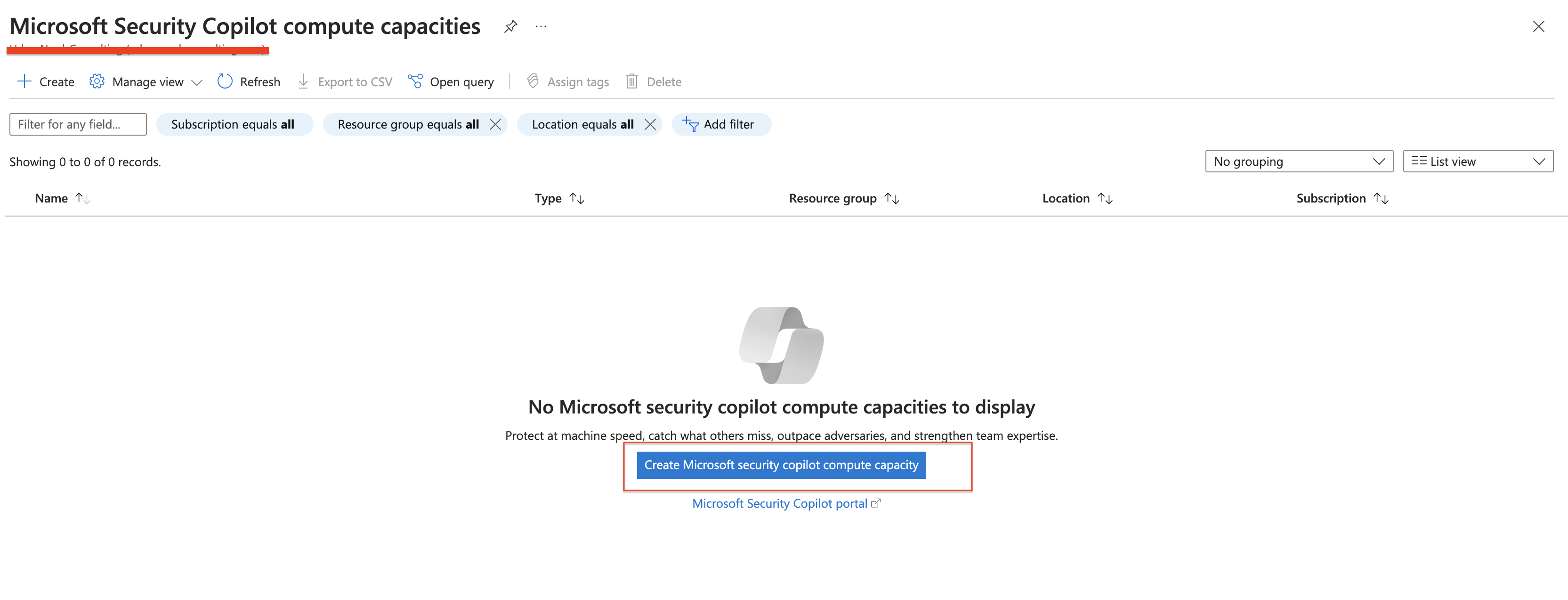
- Under Plan, choose Microsoft Security Copilot and select Create.
- Fill in the required details, including:
- Subscription and resource group.
- Capacity name.
- Prompt evaluation location.
- Number of SCUs.
- Acknowledge terms and conditions, then select Review + Create.
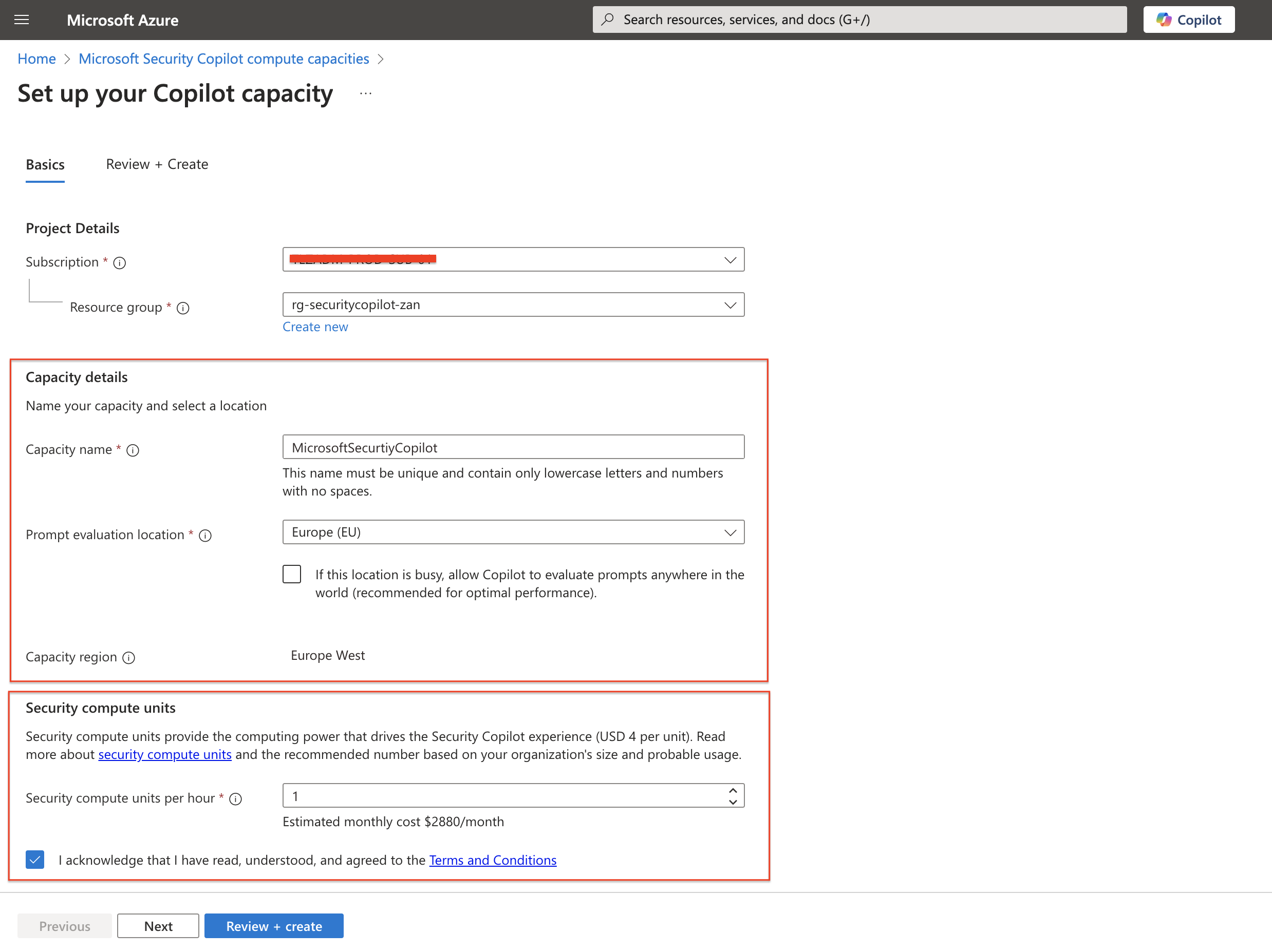
Wait for the validation to complete.
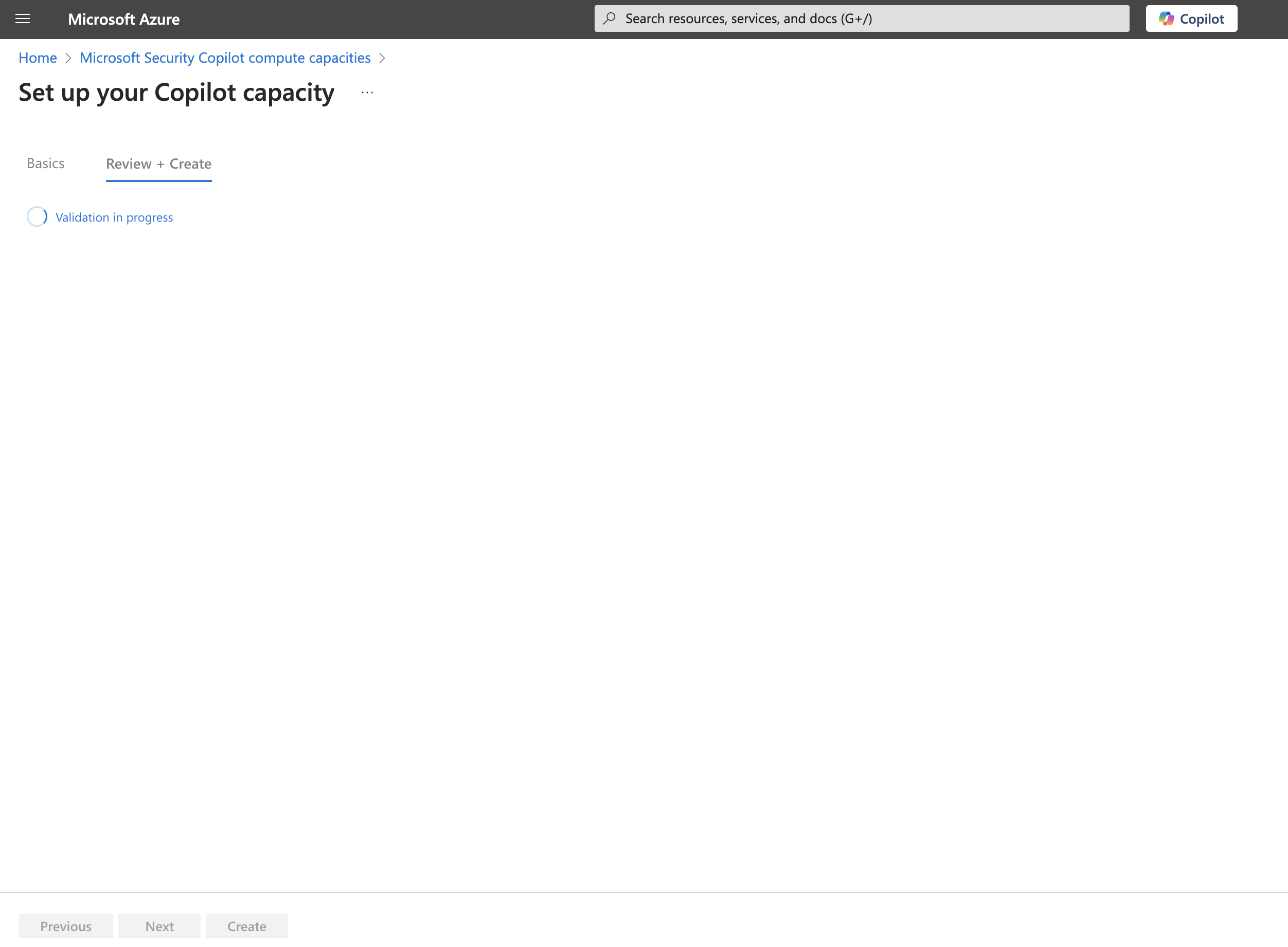
Once validation has completed, click Create.
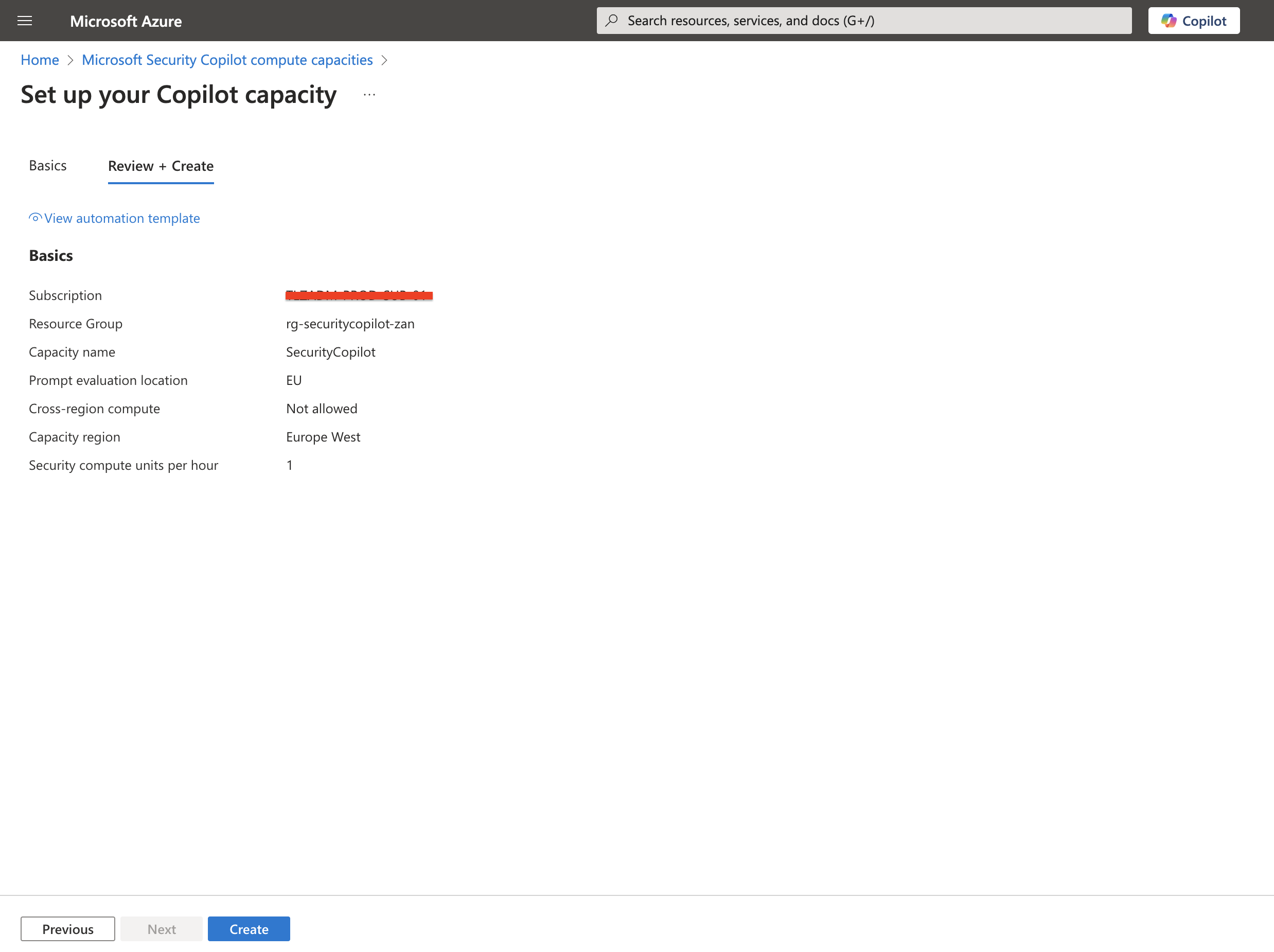
- After successful creation, navigate to the Security Copilot portal to finish setup.
Step 2: Assign Roles and Authentication in Microsoft Security Copilot
Authentication and role assignment are key to ensuring secure and efficient access to Microsoft Security Copilot. Copilot uses on-behalf-of authentication to access security-related data through active Microsoft plugins. This ensures that users can access the right data based on their permissions while adhering to the principle of least privilege.
How Authentication Works in Security Copilot
- On-Behalf-Of Authentication:
- Security Copilot accesses security data via Microsoft plugins using on-behalf-of authentication. This means that Copilot acts on behalf of the authenticated user, ensuring that data access aligns with the user’s roles and permissions.
- RBAC Overview:
- Security Copilot Roles: These roles are specific to Copilot and managed within the platform. They control access to Copilot features but do not provide access to external data.
- Microsoft Entra RBAC: Entra roles provide access across Microsoft services containing security data, such as Microsoft Sentinel and Microsoft Defender.
- Azure RBAC: Azure roles manage access to Azure resources like Security Compute Units (SCUs) and Sentinel workspaces.
Security Copilot Roles
Security Copilot introduces two specific roles:
- Copilot Owner:
- Full access to all Copilot features, including managing capacity, plugins, and configuration settings.
- Automatically inherited by users with the Global Administrator or Security Administrator roles in Microsoft Entra.
- Copilot Contributor:
- Access to create and share sessions but with limited administrative capabilities.
- Suitable for analysts and operational users needing access to Copilot sessions.
Assigning Roles in Security Copilot
Follow these steps to assign roles effectively:
Navigate to the Security Copilot portal and select the Home Menu.
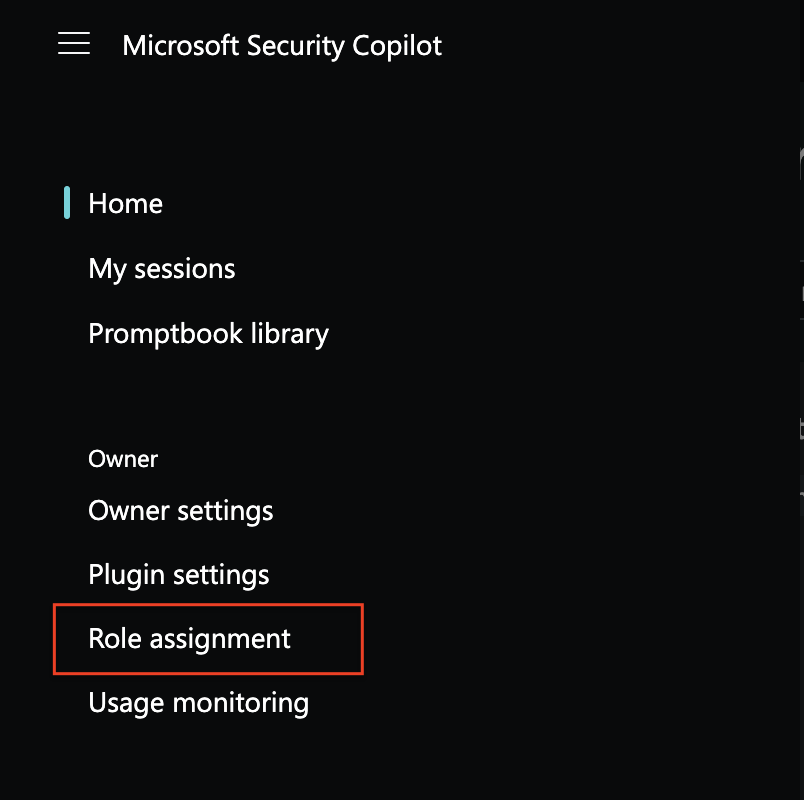
Choose Role Assignment and click Add Members.
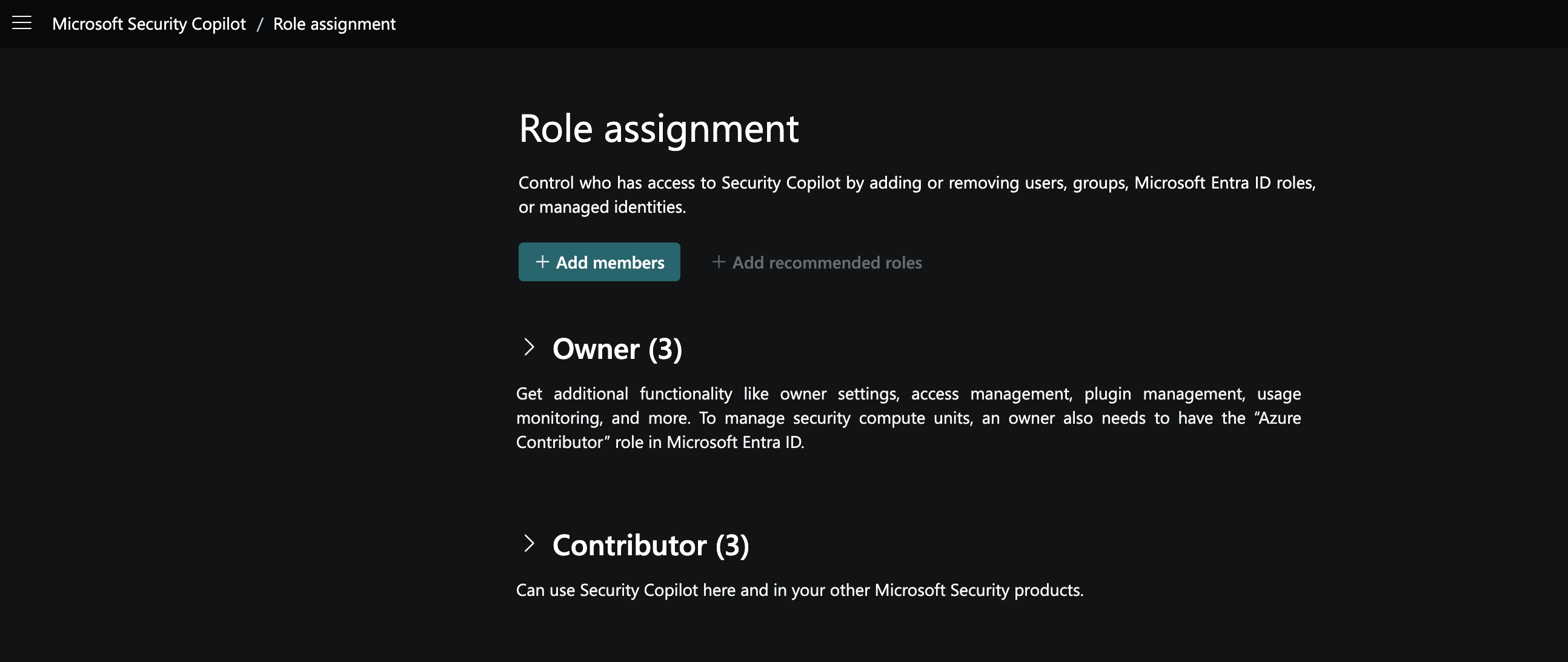
In the dialog box, type the name of the person or group you want to add.
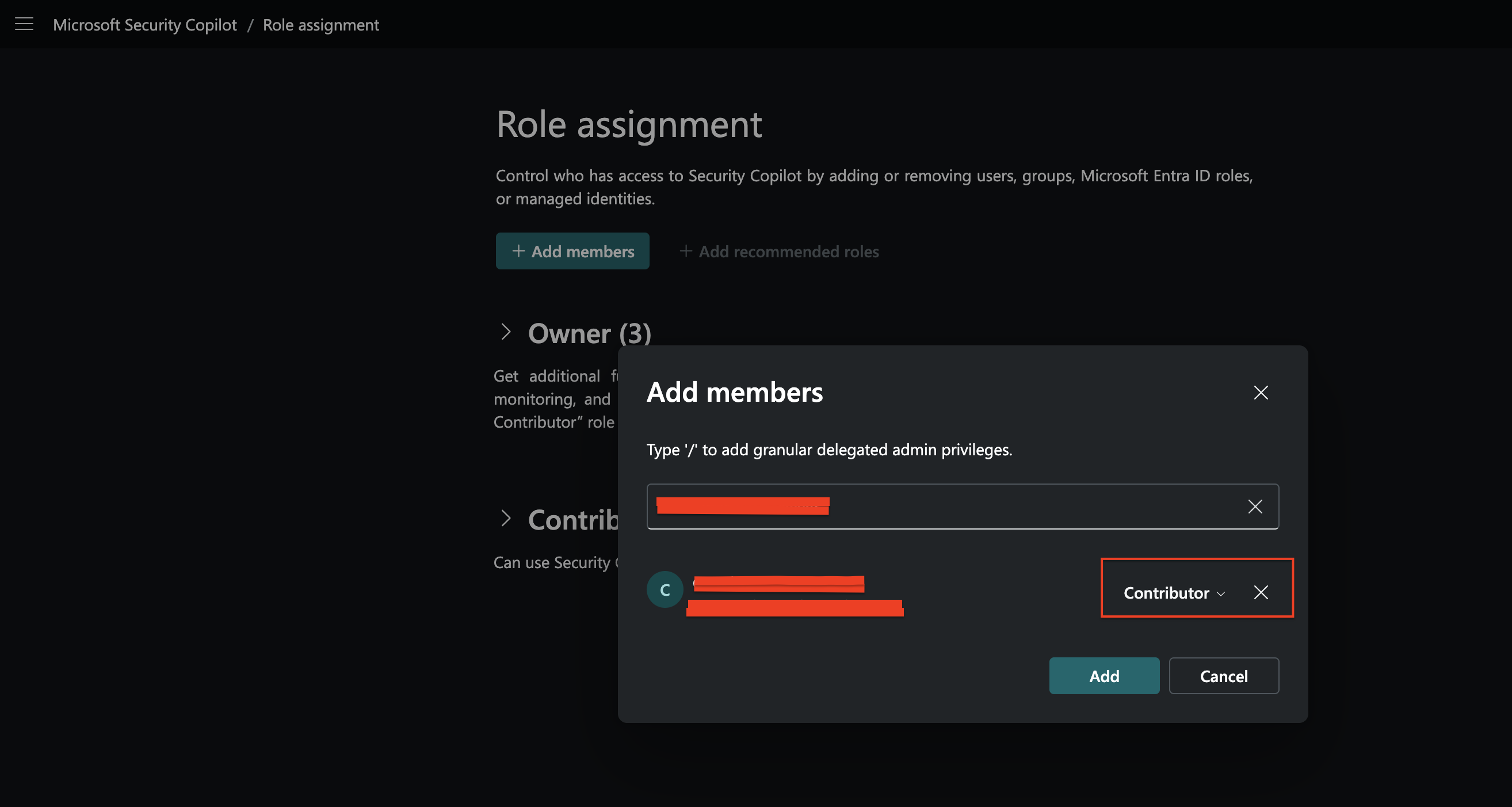
Select the appropriate role (Copilot Owner or Copilot Contributor).
Click Add to finalize the assignment.
Recommended Role Configurations
- Recommended Microsoft Security Roles:
- Use the predefined bundle of roles that include Microsoft Entra and service-specific roles like Microsoft Purview or Defender roles. This simplifies role assignment while ensuring security.
- Example: Analysts assigned the Compliance Administrator role in Microsoft Purview automatically get access to Purview plugin data.
- Custom Roles:
- For advanced scenarios, create custom roles for granular control. However, this requires additional administrative effort.
Key Role Assignment Considerations
- Avoid Broad Assignments:
- If your organization uses the default “Everyone” group, replace it with the Recommended Microsoft Security Roles for more secure and targeted access.
- Layered Permissions:
- Ensure that users have the appropriate Microsoft Entra and Azure RBAC roles for accessing plugin data.
- Security Groups:
- Use security groups instead of assigning roles to individual users to simplify management and reduce administrative overhead.
Authentication Across Plugins
Each Microsoft plugin accessed via Security Copilot has its own role requirements. Ensure users have the necessary permissions for these plugins. For example:
- Microsoft Sentinel Plugin: Requires roles like Sentinel Reader or Contributor.
- Microsoft Intune Plugin: Requires roles like Endpoint Security Manager.
- Microsoft Defender XDR Plugin: Requires appropriate Defender roles.
Shared Sessions and Multi-Tenant Access
- Shared Sessions:
- Users with the Copilot Contributor role can share sessions within the same tenant. Shared sessions are read-only and do not grant additional data access.
- Multi-Tenant Access:
- Security Copilot supports authentication across multiple tenants, enabling access to security data from different organizations.
- Example: An external member account can be assigned necessary roles to access Copilot in a merged organization.
Authentication and role assignment are key to ensuring secure and efficient access to Microsoft Security Copilot. Copilot uses on-behalf-of authentication to access security-related data through active Microsoft plugins. This ensures that users can access the right data based on their permissions while adhering to the principle of least privilege.
How Authentication Works in Security Copilot
- On-Behalf-Of Authentication:
- Security Copilot accesses security data via Microsoft plugins using on-behalf-of authentication. This means that Copilot acts on behalf of the authenticated user, ensuring that data access aligns with the user’s roles and permissions.
- RBAC Overview:
- Security Copilot Roles: These roles are specific to Copilot and managed within the platform. They control access to Copilot features but do not provide access to external data.
- Microsoft Entra RBAC: Entra roles provide access across Microsoft services containing security data, such as Microsoft Sentinel and Microsoft Defender.
- Azure RBAC: Azure roles manage access to Azure resources like Security Compute Units (SCUs) and Sentinel workspaces.
Security Copilot Roles
Security Copilot introduces two specific roles:
- Copilot Owner:
- Full access to all Copilot features, including managing capacity, plugins, and configuration settings.
- Automatically inherited by users with the Global Administrator or Security Administrator roles in Microsoft Entra.
- Copilot Contributor:
- Access to create and share sessions but with limited administrative capabilities.
- update
Recommended Role Configurations
- Recommended Microsoft Security Roles:
- Use the predefined bundle of roles that include Microsoft Entra and service-specific roles like Microsoft Purview or Defender roles. This simplifies role assignment while ensuring security.
- Example: Analysts assigned the Compliance Administrator role in Microsoft Purview automatically get access to Purview plugin data.
- Custom Roles:
- For advanced scenarios, create custom roles for granular control. However, this requires additional administrative effort.
Key Role Assignment Considerations
- Avoid Broad Assignments:
- If your organization uses the default “Everyone” group, replace it with the Recommended Microsoft Security Roles for more secure and targeted access.
- Layered Permissions:
- Ensure that users have the appropriate Microsoft Entra and Azure RBAC roles for accessing plugin data.
- Security Groups:
- Use security groups instead of assigning roles to individual users to simplify management and reduce administrative overhead.
Authentication Across Plugins
Each Microsoft plugin accessed via Security Copilot has its own role requirements. Ensure users have the necessary permissions for these plugins. For example:
- Microsoft Sentinel Plugin: Requires roles like Sentinel Reader or Contributor.
- Microsoft Intune Plugin: Requires roles like Endpoint Security Manager.
- Microsoft Defender XDR Plugin: Requires appropriate Defender roles.
Shared Sessions and Multi-Tenant Access
- Shared Sessions:
- Users with the Copilot Contributor role can share sessions within the same tenant. Shared sessions are read-only and do not grant additional data access.
- Multi-Tenant Access:
- Security Copilot supports authentication across multiple tenants, enabling access to security data from different organizations.
- Example: An external member account can be assigned necessary roles to access Copilot in a merged organization.
Assigning roles is a critical step in ensuring that users have appropriate access to Microsoft Security Copilot. Microsoft recommends assigning roles with the least privilege necessary to reduce potential security risks. Below is an overview of the available roles and how to assign them effectively.
Available Roles
- Security Administrator
- This role provides full access to Microsoft Security Copilot and its configurations. Security Administrators can manage roles, provision capacity, and configure data sharing settings.
- Reader
- This role is suitable for users who need read-only access to data and reports generated by Security Copilot. They cannot make changes to settings or configurations.
- Contributor
- Contributors can perform specific tasks such as managing SCUs or capacity without having full administrative privileges.
Steps to Assign Roles
- Sign in to the Azure Portal.
- Navigate to the Subscriptions section and select the subscription associated with your Security Copilot capacity.
- Select Access Control (IAM) from the left-hand menu.
- Click Add Role Assignment.
- Select the appropriate role (Security Administrator, Reader, or Contributor) based on the user’s responsibilities.
- Search for the user or group you want to assign the role to, then select Save.
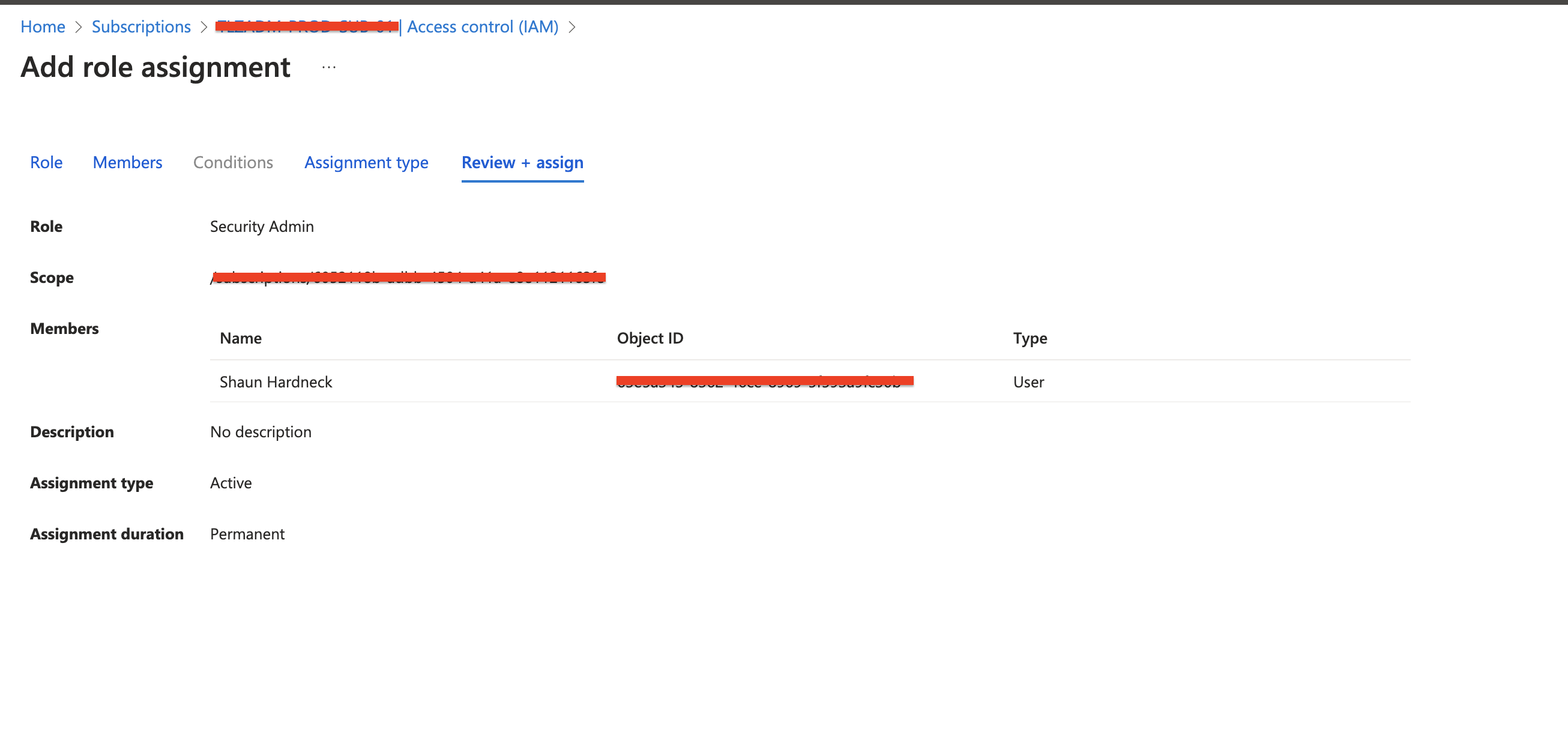
Best Practices for Role Assignments
- Always follow the principle of least privilege when assigning roles.
- Regularly review role assignments to ensure compliance with your organization’s security policies.
- Use Azure Active Directory groups for role assignments to simplify user management.
Offboarding: A Dedicated Process
Offboarding from Microsoft Security Copilot is an essential step for organizations looking to discontinue use while ensuring compliance and data security. Given its importance, offboarding can be addressed as a standalone process in this series to provide a focused guide on:
Key considerations for secure offboarding.
- Retaining critical data and managing exports.
- Best practices for removing capacity without disrupting operations.
This blog post focuses on onboarding and role assignment. A detailed guide on offboarding will be part of a future post in this series.
Wrapping Up
Thank you for joining me on this journey to get started with Microsoft Security Copilot! In this blog post, we’ve covered everything from understanding what Security Copilot is, provisioning capacity, and configuring your environment, to assigning roles and ensuring proper authentication.
This is just the beginning of your journey to mastering Security Copilot. In upcoming posts in this series, we’ll dive deeper into advanced features, best practices, and additional tools to help you maximize the capabilities of this cutting-edge AI-powered security assistant.
Remember, becoming proficient with Security Copilot is not just about setting it up, but also about continually learning and improving your organization’s security posture. Stay tuned for more tips, tutorials, and insights.
See ya on the next flight, Pilots!
Sources and Further Reading
Here are the resources I referenced to create this guide:
- Zero Trust Principles for Security Copilot
- Assign Microsoft Entra roles to users
- Managing Usage in Security Copilot
- Navigating Security Copilot Tenant Switching
- How to Become a Microsoft Security Copilot Ninja
These resources will help you deepen your understanding and fully leverage Security Copilot in your organization.
See Also
About the Author
This blog post was created by Shaun Hardneck, a Microsoft Security Architect and Consultant with a focus on Microsoft 365, Azure, and Entra ID. Shaun shares practical tips and insights through his blog, ‘ThatLazyAdmin,’ helping IT professionals navigate Microsoft technologies and improve organizational security.
When Shaun isn’t helping businesses secure their environments, he’s passionate about exploring the latest Microsoft technologies and contributing to the IT community. Connect with Shaun on LinkedIn or explore more of his work at ThatLazyAdmin.

Be First to Comment